HP-UX AAA Server A.08.00.01 Administrator's Guide
NOTE: The HP-UX AAA Server supports only the following EAP authentication
methods for OTP authentication:
• PEAP (EAP-GTC)
• TTLS (PAP and MS-CHAP v2)
The HP-UX AAA Server also supports EAP-SIM and EAP-AKA for mobile
communication networks. For information on EAP-SIM and EAP-AKA, see
Chapter 17 (page 219)
The following table lists the EAP methods the HP-UX AAA Server supports and which
of the above features each method offers. Use the table and your inventory information
to help decide which EAP method to use.
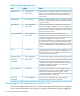
Table 13-2 Supported EAP Methods and Their Features
DescriptionFeatureEAP Method
Tunneled TLS: Can carry additional EAP or legacy
authentication methods like PAP and CHAP. Integrates with
1, 2, 3, 5, 6TTLS
the widest variety of password storage formats and existing
password-based authentication systems. Supplicants available
for a large number of clients
Protected EAP: Functionally very similar to TTLS, but does not
encapsulate legacy authentication methods.
1, 2, 5, 6PEAP
Transport Layer Security: Uses TLS (also known as SSL) to
authenticate the client using its digital certificate.
NOTE: Some supplicants require specific extensions to
support certificates for EAP.
1, 2, 4, 5TLS
Message Digest 5: Passwords are hashed using the MD5
algorithm. Can be deployed for protecting access to LAN
3MD5
switches where the authentication traffic will not be transmitted
over airwaves. Can also be safely deployed for wireless
authentication inside EAP tunnel methods (see feature 5 above).
Microsoft Challenge Handshake Accept Protocol: Passwords
are hashed using a Microsoft algorithm. Can be deployed for
2, 3MS-CHAP
protecting access to LAN switches where the authentication
traffic will not be transmitted over airwaves. Can also be safely
deployed for wireless authentication inside EAP tunnel methods
(see feature 5 above).
Generic Token Card: Carries user specific token cards for
authentication.
4, 6GTC
158 Securing LAN Access With EAP