VERITAS Enterprise Administrator (VEA 500 Series) Getting Started
Chapter 2, Using the VEA
Connecting and Disconnecting a Host
23
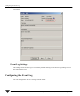
Complete the Connection dialog box as follows:
When you have provided all necessary information in the dialog box, click OK. The new host
appears in the object tree in the main window.
After you have started VEA on one host, you can connect to additional hosts from the same session.
Each host machine must be running the VEA service.
Logon Authentication
There are three authentication mechanisms by which a connection can be established with the
server where VERITAS products are installed.
◆ Silent Logon (Windows platforms only): This happens when the server is local; that is, the
VEA client and server both are running on the same machine. If the user has logged on with
administrator privileges, then username and password are not required. (The basic connection
dialog box is used.)
◆ Native Logon : Username and password are required to authenticate the user. (The expanded
connection dialog box is used.)
◆ DCOM authentication (Windows platforms only): If the user has logged in as administrator on
the domain, then username and password are not required to authenticate the user (the basic
connection box is expanded after entering the server name and clicking OK), and the user is
connected to the server. The server needs to be started with administrator privileges for this
type of authentication.
Hostname: Enter the name of the machine to be administered. (For VxVM, both
VxVM and the VEA service must be running on this machine.)
Username: Enter your login name. Only users with appropriate privileges can access
VEA on the specified machine. (The service is already running on the host.)
Password: Enter your password for the machine to be administered. Select the
“Remember Password” box to save the password on your computer.
Notes:
◆ This task requires a host machine name, user name, and password.
◆ Only users with appropriate privileges can run VEA.
◆ Entries for the user name and password must exist in the password file or corresponding Network
Information Name Service (NIS) table on the machine to be administered.