HP StorageWorks 1510i Modular Smart Array iSCSI concepts and deployment guide (431338-002, July 2008)
Table Of Contents
• More complex configurations with multiple initiators need to control access to the storage and
usually create multiple LUNs and multiple targets. Each initiator is then granted access to one or
more specific targets. Targets may be shared among groups of initiators.
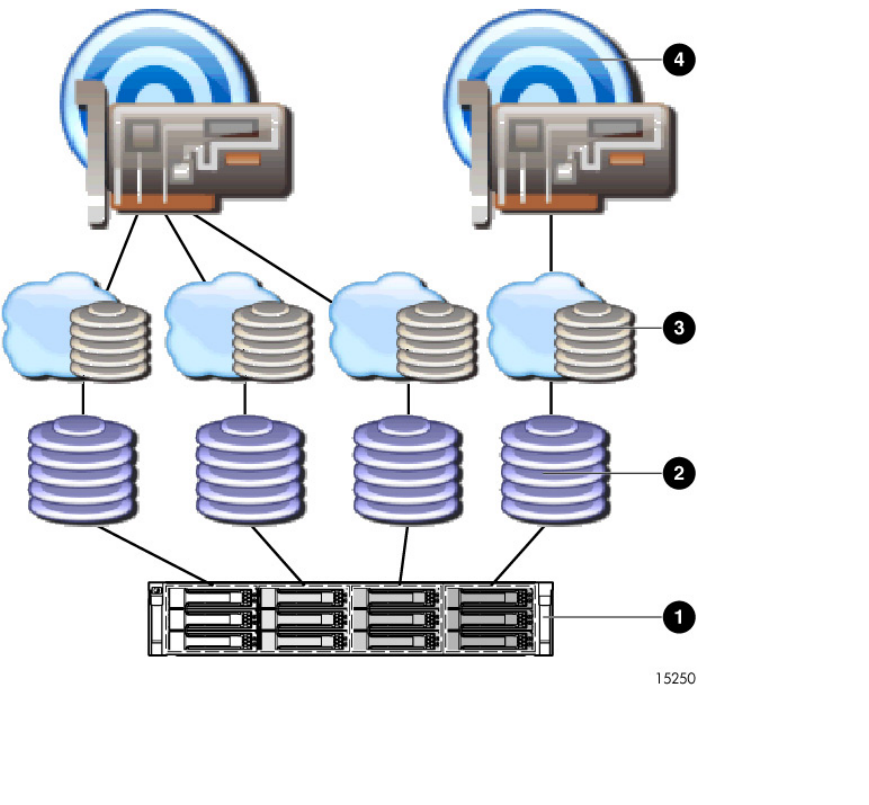
For example, the following illustration demonstrates how physical drives might be configured into four
LUNs, with three of the LUNs mapped to one target and the remaining LUN mapped, all by itself,
to a separate target.
1. Physical hard drives
2. Log
ical units (LUNs)
3. Mapped logical units
4. Storage target
Target security
To prevent unauthorized access to a storage target, all of the following security methods should be used:
• Acce
ss Control Lists (ACLs) — Each target may be configured with specific Access Controls to provide
LUN
-level access limits to only the specified initiators.
• CHAP secrets — Each target may be configured with a CHAP secret for Authentication purposes.
For more information on these and other security methods available on the MSA1510i, see Security.
24 M SA 1510 i o ve r v ie w










