HP StorageWorks 1510i Modular Smart Array iSCSI concepts and deployment guide (431338-002, July 2008)
Table Of Contents
iSCSI login ove
rview
The iSCSI login enables:
• A TCP connection for iSCSI use
• Authenticati
on of the parties
• Negotiation of the session’s parameters
• Marking the connection as belonging to an iSCSI session
An iSCSI session is established to identify all of the connections between an initiator and a target
belonging to
the same I_T nexus.
Targets list
en on a well-known TCP port (3260, as defined in the iSCSI Protocol Specification) or on a user
configured TC
P port, for incoming connections. The initiator begins the login process by connecting to
one of these
TCP ports.
An iSCSI Session has two phases:
• Login Phase
• Full Featur
ed Phase
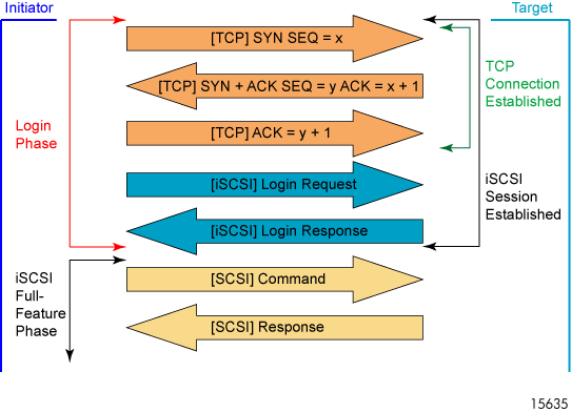
The following image illustrates an iSCSI session establishment and phases:
Login phase
The iSCSI Login Phase consists of Login requests and responses. Once authentication has occurred and
operat
ional parameters have been set, the session transitions to the Full Feature Phase and the initiator
begins performing SCSI I/Os. NOTE: Using authentication is optional.
iSCSI parameters are negotiated using Login Requests and Responses, during session establishment.
During
the Full Feature Phase, iSCSI parameters are negotiated using Text Requests and Responses. In both
cases
the mechanism is an exchange of iSCSI-text-key=value pairs (also referred to as key=value pairs).
The Login phase proceeds in two stages:
• Security/Authentication Stage — This stage consists of text exchanges using IDs, certificates, etc.,
usingkey=valuepairs. OneofthekeysthatisnegotiatedinthisstageoftheLoginphaseis
AuthMethod. For example: key=value AuthMethod=CHAP AuthMethod defines the authentication
meth
od.
• Operational Parameters Negotiation Stage — This stage consists of text string negotiation
of operating parameters using key=value pairs of login parameter exchanges. Two of the
12 i SC SI ove r view










