HP StorageWorks XP Audit Log reference guide for the XP12000/XP10000 and SVS 200 (5697-7157, November 2007)
Table Of Contents
- XP Audit Log reference guide
- Table of Contents
- About this guide
- 1 Introduction
- 2 Audit log file format
- 3 Audit log functions, operations, and products
- 4 Audit Log function
- 5 Account function
- 6 BASE function
- 7 Cache function
- 8 CFL function
- 9 CPAV function
- 10 Flex Copy XP function
- 11 LUN Security XP Extension function
- 12 ENAS function
- 13 Information function
- 14 Install function
- Add Host Group operation
- Add iSCSI Name operation
- Add iSCSI Target operation
- Add LU Path operation
- Add WWN operation
- All Config operation
- Assist Config operation
- Backup operation
- Backup Config operation
- Change Host Group operation
- Change iSCSI name operation
- Change iSCSI Target operation
- Change WWN operation
- DCR Prestaging operation
- Define Config. operation
- Delete DKC WWN operation
- Delete Host Group operation
- Delete iSCSI Name operation
- Delete iSCSI Target operation
- Delete LU Path operation
- Delete WWN operation
- DKU Emulation operation
- Force Reset operation
- Format operation
- Format Stop operation
- Init DKC iSCSI Name operation
- Initialize ORM Value operation
- Install operation
- Install CV operation
- Machine Install Date operation
- Make LUSE operation
- Make Vol./Vol. Init operation
- Micro Program operation
- MP Install operation
- M/F DCR operation
- New Installation operation
- Open DCR operation
- Patch Edit operation
- Release LUSE operation
- Restore operation
- Restore Config. operation
- Set Battery Life operation
- Set Channel Speed operation
- Set CommandDev operation
- Set CommandDevSec operation
- Set Fibre Address operation
- Set Fibre Topology operation
- Set Host Mode operation
- Set IP Address operation
- Set Security Switch operation
- Set Speed Mode operation
- Set Subsystem Time operation
- System Option operation
- System Tuning operation
- Uninstall operation
- Update Config operation
- Volume to Space operation
- 15 On Demand function
- 16 Logical Device (LDEV) function
- 17 LUN Manager (LUNM) function
- Add Host Group operation
- Add iSCSI Name operation
- Add iSCSI Target operation
- Add LU Path operation
- Add WWN operation
- Auth Info (Host) operation
- Auth Info (Target) operation
- Change Host Group operation
- Change iSCSI name operation
- Change iSCSI Target operation
- Change WWN operation
- Delete DKC WWN operation
- Delete Host Group operation
- Delete iSCSI name operation
- Delete iSCSI Target operation
- Delete LU Path operation
- Delete WWN operation
- Init DKC iSCSI Name operation
- Set Authentication operation
- Set Channel Speed operation
- Set CommandDev operation
- Set CommandDevSec operation
- Set FCSP Host operation
- Set FCSP Port Info operation
- Set FCSP Port Switch operation
- Set FCSP Target operation
- Set Fibre Address operation
- Set Fibre Topology operation
- Set Host Mode operation
- Set IP Address operation
- Set iSNS operation
- Set Security Switch operation
- Set Speed Mode operation
- Set TCP/IP Port operation
- 18 Logical Unit Number Expansion (LUSE) function
- 19 Maintenance function
- Blockade operation
- Correction Copy operation
- Drive Interrupt operation
- Format operation
- Format Stop operation
- Recover operation
- Replace operation
- Restore operation
- Restore Data operation
- Size Change operation
- Spare Disk operation
- Switch SVP operation
- Transfer Config operation
- Type Change operation
- Verify operation
- Verify Stop operation
- 20 Performance Control Base Monitor function
- 21 PORT function
- 22 Optional Product (PP) KEY function
- 23 Remote Control Unit (RCU) function
- 24 Serverless Backup Enabler (SBE) function
- 25 Volume Shredder (SHRED) function
- 26 Business Copy XP function
- 27 ShadowImage (SI) z/OS function
- 28 SNMP function
- 29 Performance Control function
- 30 Continuous Access XP function
- 31 TrueCopy (TC) z/OS function
- 32 Continuous Access XP - Journal function
- 33 Universal Replicator (UR) z/OS function
- 34 External Storage XP function
- 35 Virtual LVI / Virtual LUN (VLL) function
- 36 Auto LUN (ALUN) function
- 37 HP Disk/Cache Partition function
- 38 Volume Retention Manager (VRM) function
- 39 Volume Security (VSEC) function
- 40 V Volume (VVOL) function
- 41 XRCR function
- A Audit log file output by function
- Index
• In the United States, the Sarbanes-Oxley (SOX) Act establishes corporate accountability for all
public companies, requiring strict IT controls and processes. Specifically, Sarbanes-Oxley requires
companies to “Audit unauthorized access, misuse and fraud, in order to ensure the accuracy of
corporate financial and business information” and “maintain financial records for seven years.”
• Internationally, the Basel II Accord requires all internationally active banks to adopt similar or
consistent risk management practices. Banks are required to implement a comprehensive program
of risk prevention, detection, analysis and management, and mitigate operational risks associated
with IT systems by 2006. The accord recommends “retaining activity logs for 3 to 7 years.”
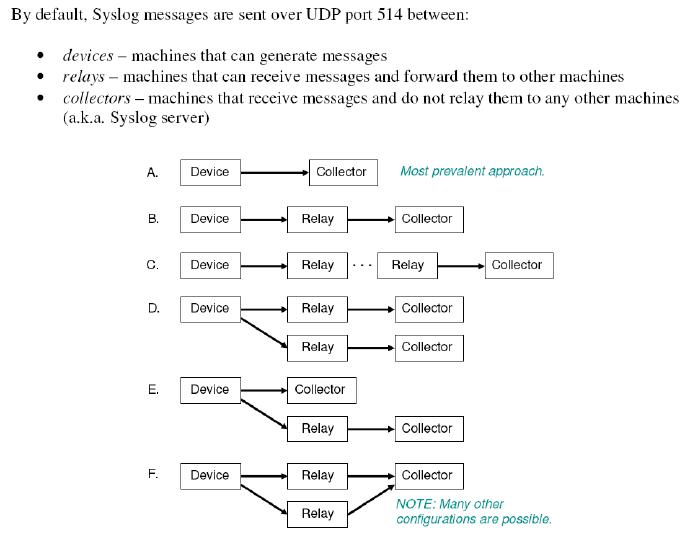
Introduction to the syslog server
Audit log uses the syslog server, which is a commonly-used simple utility and protocol, to exchange
log messages. The term syslog is often used for the protocol, the tools that send the logs, as well as
the individual logs and the log files themselves.
The syslog architecture can be summarized as follows:
• Senders (devices and relays) send messages to relays or collectors with no knowledge of whether
it is a collector or relay.
• Senders may be configured to send the same message to multiple receivers.
• Relays may send all or some of the messages that they receive to a subsequent relay or collector.
If relays do not forward all of the messages, they are acting as both a collector and a relay. In
the following figure, these devices are designated as relays.
• Relays may also generate their own messages and send them on to subsequent relays or collectors.
In that case, it is acting as a device.
The following figure illustrates some common syslog configurations.
Figure 1 Examples of syslog architecture
The specific needs of your particular business will determine the system architecture. From a storage
perspective, knowing where the log events need to be shipped, how the events need to be handled,
and then implementing it appropriately represents the end point. The storage layer need only concern
Introduction26










