Integrated Lights-Out 3 Virtual Serial Port configuration and operation HOWTO, 6th edition
Table Of Contents
- Introduction
- Conceptual overview
- Security
- Configuration
- Operation
- Known issues
- For more information
- Call to action
3
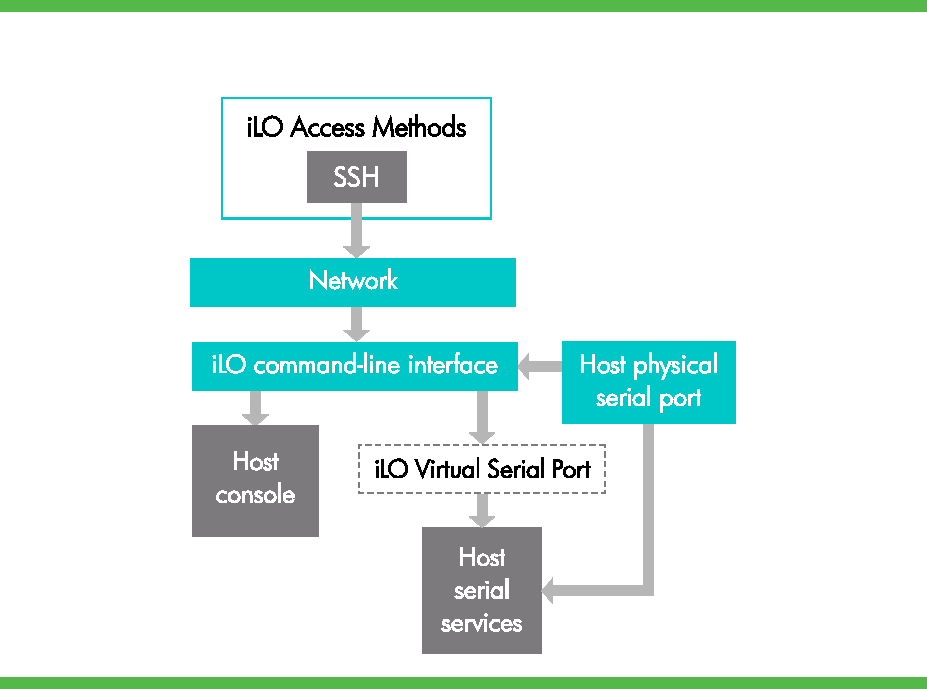
Figure 1 shows the relationship of the elements of iLO VSP. It also shows how the two iLO interfaces work
through their different access methods to enable the iLO VSP.
Figure 1. Diagram of iLO VSP interfaces
Security
iLO uses 128-bit SSL and SSH frameworks to ensure privacy of iLO actions, depending on the access
modes and types of functions being performed. Within these frameworks, iLO supports RC4, 3DES, and
AES ciphers. Key exchange uses RSA/Diffie-Hellman, and keys rotate every 3 minutes. Certificates are
generated using 1024-bit RSA keys signed with MD5RSA and using a SHA1 fingerprint.










