Insight Remote Support 7.0.9 Security White Paper
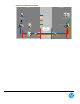
Figure 7: Remote Access Connection System Details
HP
Remote Access
Connection System
Workstation
HP Support
Specialist
Remote Access
Portal (RAP)
Remote Connectivity
Toolbox (RCTS)
Remote
Connectivity
Database
Remote Access
Connection System
(RACS, Regional)
HP Customer
Account Manager
Remote Device Access connection
User authentication and authorization data flow
Company access authorization management and connection configuration
HP routing
device
HP
Firewall
A Remote Access Connection System (RACS) is an SSH server that can forward an SSH connection to an appropriate CAS.
When the HP support specialist connects and is authenticated to the RACS, the SSH server on the RACS checks the security
token issued by the RAP to ensure that the support specialist is allowed to connect to the customer’s IP address. Upon
successful authorization, the RACS will forward the SSH connection to the HP routing device. RACS servers are located in
various HP data center locations.
Access Controls Onsite
For a primary defense, the customer external firewall can be configured to allow only RACS systems at HP to access their
VPN devices and/or CASii. Although standard passwords can be used, it is recommended to configure SSH public/private
keys instead. Some versions of SSH servers can be configured to use HP’s DigitalBadge certificates for authentication. HP
recommends that customers use the HP provided Virtual CAS, as this provides richer access control for customers.
One-time password systems, such as RSA’s SecurID, can also be used if the customer’s SSH server supports them.
The CAS itself provides the second layer of defense. Depending on the CAS type, customers can define named employees,
target systems, or even ports that HP support specialists are allowed to connect to.
The customer owns the security policies and access control into his/her environment and can specifically restrict
connections to named HP support personnel and can terminate connections as needed.
The HP Support specialist is also subject to the customer’s own access control and security policies in that the customer
must provide login credentials if needed for the device that HP wishes to connect to. For example if the HP support
engineer wishes to logon to a UNIX server within the customer’s network, the customer provides the logon name and