Insight Remote Support 7.0.9 Security White Paper
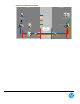
Figure 5: Virtual CAS
X86/64 Hardware
Vmware ESX
Virtual CAS
8765432187654321
UID
21
G5
HP
ProLiant
DL580
Ubuntu Linux
Software CAS
HP Engineer
CAS Administrator
Advanced
Packaging
Tool
Repository
VeriSign
Certificate
Revocation
List
Web Server
Customer Access
Server VMware host
CAS Virtual View
Administrator Access to SW CAS User Interface (GUI)
CRL check to www.verisign.com
Software Updates from APT Repository (at HP)
Tunneled application traffic from HP to Target host
SSH Traffic from HP to SW CAS for Authentication
tcp 443/HTTPS - Internal
tcp 80/HTTP - Outbound
tcp 443/HTTPS - Outbound
tcp/App Specific - Inbound
tcp 22/SSH - Inbound
To Target
Host
Vmware ESX
VM Guest OS
Application
User
Interface
HP Instant Customer Access Server (iCAS)
HP Instant Customer Access Server (iCAS) is a lightweight connection tool that allows an HP support agent to quickly and
securely connect to a customer's environment to aid in diagnosis and repair of supported hardware devices. The customer
runs the iCAS software as a browser plug-in on any Windows or Linux computer which has network access to the device the
HP support engineer is attempting to access. HP iCAS uses a meet-in-the-middle connection paradigm to facilitate the
remote access session by establishing a tunneled SSH session to a Remote Access Meeting Server (RAMS). The HP engineer
generates a unique connection key that is used to couple the HP Engineer and Customer SSH connections together creating
an end-to-end SSH tunnel between the HP Support engineer desktop and the iCAS host. Once the session key is exchanged,
the session is established as follows:
• HTTPS connection occurs (using TCP/443) from iCAS host to RAMS using URL and Session key provided by HP Support
engineer
• Customer’s SSH connection (using TCP/ 2022) is tunneled via HTTPS to RAMS Server
• The HP engineer session sees the customer session connected to the RAMS
• An HTTPS connection is made from HP engineer browser to the RAMS
• The HP engineer’s SSH connection (using TCP/2022) is tunneled via HTTPS to RAMS
• The unique session key insures that both sessions rendezvous on the RAMS and create a secure SSH tunnel
From this point the HP engineer can request access to the affected system in the customer network by tunneling through
the SSH tunnel (inside the HTTPS tunnel) to the target device inside the customer network. The customer must specifically
grant access and provide the access credentials to the HP engineer before the connection to the target device can be
established.