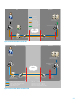
7.0.8 Insight Remote Support Security White Paper
26
CustomerHP
Customer target
systems or devices
Customer Access
Server
Internet
HP Support
Specialist
Tunneled application traffic to target system Application specific – inbound
Raw application traffic to target system Application specific – inbound
SSH tunnel from HP to CAS TCP/22 (SSH) – inbound
Customer
Firewall
HP
Firewall
Support
Specialist
Workstation
Remote Access
Connection System
Figure 8: SSH Direct
Connectivity Methods for VPN Solutions
Many customers’ security policies require that all inbound connections be protected inside a VPN connection that is
terminated in their DMZ. HP offers a site-to-site IPSec VPN access solution for unattended RDA. SSH port-forwarding is
still used, except that it is tunneled over IPSec using VPN routers. The combination of SSH and IPSec provides enhanced
Internet security. SSH is recommended as it provides better end-to-end security as well as enhanced functionality (file
transfer capabilities and application tunneling), but HP recognizes that this may not fit all security policies. Therefore,
we offer site-to-site IPSec VPN connectivity with and without SSH tunneling. The following figures show both options.