7.0.8 Insight Remote Support Security White Paper
23
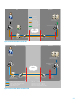
connections together creating an end-to-end SSH tunnel between the HP Support engineer desktop and the iCAS host.
Once the session key is exchanged, the session is established as follows:
HTTPS connection occurs (using TCP/443) from iCAS host to RAMS using URL and Session key provided by HP Support
engineer
Customer’s SSH connection (using TCP/ 2022) is tunneled via HTTPS to RAMS Server
The HP engineer session sees the customer session connected to the RAMS
An HTTPS connection is made from HP engineer browser to the RAMS
The HP engineer’s SSH connection (using TCP/2022) is tunneled via HTTPS to RAMS
The unique session key insures that both sessions rendezvous on the RAMS and create a secure SSH tunnel
From this point the HP engineer can request access to the affected system in the customer network by tunneling
through the SSH tunnel (inside the HTTPS tunnel) to the target device inside the customer network. The customer must
specifically grant access and provide the access credentials to the HP engineer before the connection to the target
device can be established.
Figure 6: Instant CAS (iCAS)