A.05.80 HP Insight Remote Support Advanced and Remote Device Access Security Overview (October 2012)
Security Overview
Appendix A: X.509 Certificates and Insight Remote Support Advanced
signature using the CA’s public key (that is, the CA’s certificate). If the certificate’s private key has been
stolen, the certificate can be revoked by the CA. The CA maintains revoked certificates in a Certificate
Revocation List (CRL). The CRL, which is a list of revoked certificates’ serial numbers, is signed by the
CA. For a user to validate a certificate, he/she must have a priori knowledge of the CA’s certificate.
Digital Signature Verification in the Remote
Support Client
Signature Checking
The Remote Support Client (RSC) running on the CMS connects to a server at HP,
https://services.isee.hp.com, using SSL or TLS. The server signs a message containing a copy of its
X.509 certificate and returns the message to the RSC. The RSC must then verify the identity of the
server:
1. The client checks the validity period of the server’s certificate. If the current date is not between the
start and end times of the certificate, the check fails.
2. Using the public key contained in the server’s certificate the client checks the message’s digital
signature. Failure at this point causes validation failure.
3. The client attempts to verify the server’s certificate. This is done by finding the certificate of the
server certificate’s issuer. This issuer’s certificate can be sent along with the server’s certificate or
stored locally on the client. (Most web browsers have a built-in certificate store of well-known
certificate issuers.) If the issuer’s certificate is found and it verifies the server certificate’s signature,
the verification process continues.
4. The issuer’s certificate must now be verified. There are two ways this can go:
a. If the issuer’s certificate is a CA root certificate, the client must have a copy of it for verification.
The client cannot rely on a root certificate that was sent along with a server certificate.
b. If the issuer’s certificate is not a CA root certificate, the client can use either the issuer’s
certificate sent from the server or one stored locally.
5. The issuer’s certificate is checked just as the server’s certificate is checked in steps 1, 2, and 3.
Failure in any of these steps causes verification failure.
6. The recursive process of steps 4 and 5 (and hence, 1, 2, and 3) are repeated until the CA root
certificate is encountered.
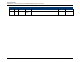
In practice, most server certificates are no more than three levels deep. For example,
services.isee.hp.com has the following certificate chain:
VeriSign Class 3 Public Primary CA
VeriSign Class 2 Secure Server CA - G2
services.isee.hp.com (g1w3054g.austin.hp.com)
Figure A.1. Insight Remote Support (example)
HP Insight Remote Support Advanced and Remote Device Access (A.05.80)Page 53 of 97