HP Imaging and Printing Security Center 2.0 - Instant-On Security
7
An enabled Device Announcement Agent announces when the device is powered up on the
network for the first time. Announcements also occur during a device power cycle, cold
reset, IP address change and link down/link up scenario.
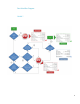
DAA Workflow Description
The Device Announcement Agent is enabled by default. The device is capable of displaying
four different DAA states; Disabled, In Progress, Success or Failed. Success indicates the
device was able to discover an HP IPSC server and establish communication. Failed,
indicates the device was not able to discover an HP IPSC server or was not able to establish
a connection with a discovered HP IPSC server. Use the following DAA workflow
description and the diagram in Figure 7 below to understand the device announcement
experience:
1. A supported device is powered up on network with a pre-configured IP address or
automatically acquires an IP address after network installation. The DAA is enabled
by default on the device, but can easily be disabled if Instant-On Security is not
desired. In the disabled scenario, the device will show a Disabled status for the
announcement agent.
2. If the DAA is enabled, and the IPSC server IP address is configured on the device,
the device will target the provided IPSC server IP address to begin Instant-On
communication. If the IPSC server IP address is not configured on the device, the
device will attempt DNS IP resolution of the following hostname or DNS alias
(CNAME): hp-print-mgmt. Note: This hostname or alias must be
administratively assigned to the IPSC server for successful default Instant-On
functionality.
3. The IPSC server Instant-On feature must be enabled and configured to allow DAA
communication to proceed without failure. The Instant-On feature can be configured
to discover only or discover, assess and remediate.
4. With the IPSC server IP address known (either through direct configuration or DNS
resolve), TCP port 3329 communication is attempted with the IPSC server. The
device announces itself using SSL and its self-signed identity certificate.
5. Upon receiving the announcement, the IPSC configuration server authenticates the
device, retrieves the device’s identity details and adds the device to the database.
IPSC then continues with an assessment of the device based upon the designated
IPSC security policy and remediates the device’s non-compliant security settings.