HP Data Protector 6.2 software integration with HP 3PAR Storage System
39
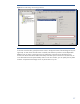
Figure 36: Select a backup policy
The next step is to specify the media to be used for the backup.
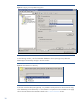
In the next window (see Figure 37), it is possible to specify application-specific options such as:
• Pre-exec and Post-exec executables that will be started before and after the backup is done. These
executables will be started at the node where the DAG Virtual IP address is pointing to at the time
of the backup.
• Consistency check options. After the virtual copy is created and exported/presented to the backup
host, Data Protector will start the consistency check of the database file and log files. The
consistency check creates a heavy I/O load on the storage system. It is possible to reduce this I/O
load by introducing a pause of 1 second after a specified number of I/O operations. To further
reduce the I/O load and to increase the backup speed, Data Protector provides the possibility to
omit the consistency check completely or to run a consistency check of log files only. However, it is
highly recommended to run a consistency check on both database and log files. By default, Data
Protector will run a consistency check of log files only.
After backup completes successfully, Exchange Server 2010 truncates the backed up logs on all
servers that are part of the DAG. Logs that have not yet been applied to all DAG copies are not
truncated. Exchange Server 2010 truncates logs after full and incremental backups. However, it does
not truncate logs after copy backups.