HP Device Manager 4.6 - Installation and Update Guide
Overview
This document discusses the installation of HP Device Manager (HPDM) and the usage of HPDM tools in a Proof of Concept.
Production installation might differ based on a number of parameters, including, but not limited to, the number of remote
sites, the number of devices, LAN and WAN links, network configuration, and such. Contact your device technical consultant
for more details.
HPDM consists of the following components:
• HPDM Console—The graphical application used by administrators to access the management system.
• HPDM Server—The central server, which consolidates and controls all management activities.
• HPDM Gateway—The link between HPDM Agents and the HPDM Server.
• Master Repository Controller—The content manager in the Master Repository, which synchronizes that content to
other repositories as requested by the HPDM Server.
• HPDM Agent—Software installed on the client to enable device management.
The HDPM Console, HPDM Server, HPDM Gateway, and Master Repository Controller can be installed on the same machine
or on separate machines.
HPDM Server preparation
For this setup, you need either Windows Server 2003 or Windows Server 2008 running on either a physical or virtual
machine. Allocate at least 10 GB for the operating system and the HPDM files. Full server recommendations are available in
the HP Device Manager 4.6 Administrator Guide.
This paper assumes that the HPDM Server will use a standard installation without any additional services running.
This chapter focuses on the post-installation steps of installing HPDM onto Windows Server 2008 R2. The example assume
a complete HPDM installation has already been performed on the HPDM Server and that a user account for the FTP
transactions has already been created.
FTP server configuration
For details about FTP server configuration, see the HP Device Manager 4.6 FTP Server Configuration white paper.
Windows Firewall settings
In Windows Server 2008 R2, the built-in firewall service helps secure your server from network threats and is enabled by
default. If you use the built-in Windows Firewall, you need to configure your settings so that the HPDM and FTP traffic can
pass through the firewall. Note that you need to be logged on as Administrator or as a user that has administrator privileges
to configure the firewall. If not logged on as Administrator, be sure to click Start > All Programs > Accessories > Command
Prompt, and then right-click Command Prompt and select Run as Administrator. This is required because User Account
Control (UAC) in the Windows Server 2008 R2 operating system prevents non-Administrator account access to the firewall
settings.
Firewall settings for FTP
You must configure an exception for both the control channel (port 21) and the port range for the passive data channel. This
can be done in the GUI for the Windows Firewall, but it is easier to add these rules from the command line.
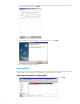
To configure the Windows Firewall setting for FTP using the command line:
1. Click Start > All Programs > Accessories > Command Prompt. If not logged on as Administrator, be sure to right-click
Command Prompt and select Run as Administrator.
2. To add an inbound rule for the command channel and to allow connections to port 21, enter the following command
and then press Enter:
netsh advfirewall firewall add rule name="FTP (non-SSL)" action=allow
protocol=TCP dir=in localport=21
3. To disable stateful FTP filtering so that Windows Firewall does not block FTP traffic to the passive port range, enter the
following command and then press Enter:
netsh advfirewall set global StatefulFtp disable
3