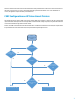
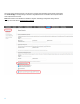
HP FutureSmart - Preventing cross site request forgery (CSRF) attack using CSRF-tokens (white paper)
7
public class Level1Controller : ExtWebContentControllerBase
{
/// <summary>
/// web request entry point
/// </summary>
public override void Load()
{
string token = string.Empty;
if (ExtContext.SessionState.GetData.ContainsKey("CSRFToken") &&
ExtContext.SessionState.GetData["CSRFToken"] != null)
{
token = SessionState.GetData["CSRFToken"].ToString();
}
…
}
}
In the above example, the non-empty “token” variable will be a valid CSRFToken that can be passed back to a client, and
which can then be passed back into the EWS for a subsequent HTTP POST request.
References
https://www.owasp.org/index.php/Cross-Site_Request_Forgery_(CSRF)
https://www.owasp.org/index.php/Cross-Site_Request_Forgery_(CSRF)_Prevention_Cheat_Sheet
hp.com/go/support
Current HP driver, support, and security alerts
delivered directly to your desktop
© Copyright 2016, 2017 HP Development Company, L.P. The information contained herein is subject to change without notice. The only warranties
for HP products and services are set forth in the express warranty statements accompanying such products and services. Nothing herein should be
construed as constituting an additional warranty. HP shall not be liable for technical or editorial errors or omissions contained herein.
Doc ID: c05428973
Created November 2016
Version 2.2 April 2017
Public