HP FutureSmart - Preventing cross site request forgery (CSRF) attack using CSRF-tokens (white paper)
3
The Server verifies if the token from the client matches the token provided earlier to the client for the current session. If
the token is not-present or not-correct, the request would be rejected with “HTTP 403” error. If the “CSRFToken” is
correct, the application request would be processed further.
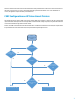
CSRF Configuration on HP FutureSmart Printers
HP FutureSmart devices enforce CSRF protection by default. When this protection is enforced, all the incoming POST
requests would be checked presence for of Origin header or Referer header. If they are present, they would be checked for
correctness and allowed origin (that is the host-device).
Further, the HTML contents would be checked for CSRF token. If CSRF token verification is successful, the request would
be processed further. If the verification fails, the request would be rejected by the server.
Start
(Incoming HTTP
POST)
Has Origin Header
Has Referer
Has CSRFToken
Header with valid
token
Reject HTTP request - 403
Process HTTP Request
No
No
No
Yes
Yes
Header has
authorixed origin
info
Yes
Referer Header has
authorized host/
URI
No
Yes
Yes