Datasheet
Book IV
Chapter 1
Network Security
Terminology
461
Looking at Security Devices
automatically, infecting each computer. How the virus spreads depends on
the virus itself — there have been worm viruses that connect across the
network automatically to a vulnerable system and then infect that system.
Recently, worm viruses automatically infect a flash drive that is connected
to the system so that when you take the drive to the next system, the worm
infects that system from the flash drive.
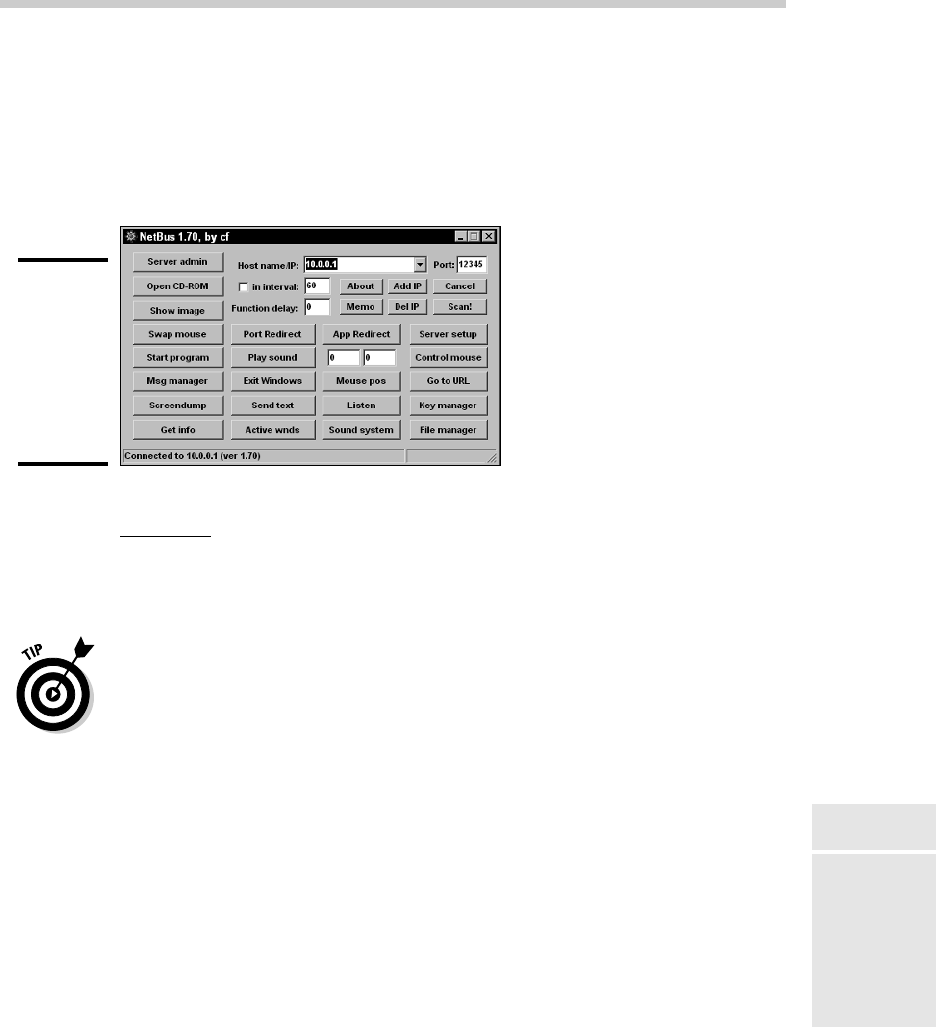
Figure 1-3:
Using a
Trojan virus
known as
NetBus
to control
a user’s
computer.
Logic bomb
A logic bomb is a type of virus or malicious software that was designed to
wreak havoc on your system on a certain date and time. The scary thing
about logic bombs is that they seem like useful software until the day the
programmer decides it will become malicious!
To protect against malicious software such as a virus, Trojan horse, worm,
and a logic bomb, you need to use a firewall and keep your virus definitions
up-to-date.
Looking at Security Devices
When looking to secure your systems or networks, you can definitely follow
best practices such as patching systems or using strong passwords, but
realistically, you are going to need to use one or more popular security
devices to secure your environment. In this section, I discuss popular security
devices you should be familiar with for the CCENT certification exam.
Firewalls
A firewall is a piece of software or a device that is designed to control what
traffic is allowed to enter or leave the network. Most firewalls control traffic
that enters the network by analyzing the header of the packet and looking at
the source IP address, destination IP address, and the source and destination
port. If the packet trying to enter the network meets certain conditions, such
22_647486-bk04ch01.indd 46122_647486-bk04ch01.indd 461 10/15/10 11:27 PM10/15/10 11:27 PM










