Deployment Guide
Table Of Contents
- Table of Contents
- Preface
- About Extreme Campus Controller Deployment
- Configuring DHCP, NPS, and DNS Services
- Centralized Site with a Captive Portal
- Centralized Site with AAA Network
- Deploying a Mesh Network
- Configuring an External NAC Server for MBA and AAA Authentication
- Manage RADIUS Servers for User Authentication
- External Captive Portal on a Third-Party Server
- Access Control Rule Admin Portal Access
- Deploying Centralized Web Authentication
- Deploying ExtremeCloud IQ - SE as an External Captive Portal
- Deployment Strategy
- Configuring an External Captive Portal Network
- Editing the Configuration Profile for Network and Roles
- Extreme Campus Controller Default Pass-Through Rule
- Adding Extreme Campus Controller as a Switch to ExtremeCloud IQ - Site Engine
- Editing the Unregistered Policy on ExtremeCloud IQ - Site Engine
- Editing the ExtremeCloud IQ - Site Engine Profile for Policy and Location-Based Services
- Deploying an ExtremeGuest Captive Portal
- Deploying Client Bridge
- Deploying an Availability Pair
- Deploying Universal APs
- Extreme Campus Controller Pair with ExtremeLocation and AirDefense
- ECP Local Authentication
- PHP External Captive Portal, Controller’s Firewall Friendly API
- Index
Creating an Engine Rule
Create a unique engine rule that applies the Enterprise User role upon authentication.
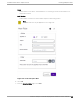
1. Go to Onboard > Rules > Add and configure the following parameters:
Name
test2-rule
Rule Enabled
Select this box to enable the rule.
Location Group
Specify the Test2-AAA Network we created.
2. Select Enterprise User as the Accept Policy.
3. Click Save.
Next, create a unique policy role that this engine rule will apply upon authentication instead of
Enterprise User.
Related Topics
Creating a Policy Role on page 67
Creating a Policy Role
You can create a policy role that will customize network access.
To create a new policy role:
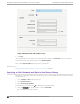
1. Go to Configure > Policy > Roles > Add and configure the following parameters.
Name
myTest2-policy
Default Action
Set to Deny.
The policy rule will deny everything except for the rules we define as allowed.
2. Select the L3 L4 Rules section and click New.
3. Configure the following rules:
• Allow trac to subnet 0.0.0.0/0, any protocol, Port DHCP Server (68).
• Allow trac to subnet 0.0.0.0/0, any protocol, port Port DHCP Client (67).
• Allow trac to subnet 10.48.51.50/28, any protocol, any port.
• Allow trac to subnet 10.48.49.9/32, any protocol, any port.
4. Click Save to save the policy.
5. Go to Onboard > Rules.
6. Edit the test2-rule Accept Policy. Apply myTest2-policy instead of Enterprise User policy.
a. Highlight test2-rule and click
.
b. From the Accept Policy field, select myTest2-policy.
Centralized Site with AAA Network
Creating an Engine Rule
Extreme Campus Controller Deployment Guide for version 5.46.03 67