Deployment Guide
Table Of Contents
- Table of Contents
- Preface
- About Extreme Campus Controller Deployment
- Configuring DHCP, NPS, and DNS Services
- Centralized Site with a Captive Portal
- Centralized Site with AAA Network
- Deploying a Mesh Network
- Configuring an External NAC Server for MBA and AAA Authentication
- Manage RADIUS Servers for User Authentication
- External Captive Portal on a Third-Party Server
- Access Control Rule Admin Portal Access
- Deploying Centralized Web Authentication
- Deploying ExtremeCloud IQ - SE as an External Captive Portal
- Deployment Strategy
- Configuring an External Captive Portal Network
- Editing the Configuration Profile for Network and Roles
- Extreme Campus Controller Default Pass-Through Rule
- Adding Extreme Campus Controller as a Switch to ExtremeCloud IQ - Site Engine
- Editing the Unregistered Policy on ExtremeCloud IQ - Site Engine
- Editing the ExtremeCloud IQ - Site Engine Profile for Policy and Location-Based Services
- Deploying an ExtremeGuest Captive Portal
- Deploying Client Bridge
- Deploying an Availability Pair
- Deploying Universal APs
- Extreme Campus Controller Pair with ExtremeLocation and AirDefense
- ECP Local Authentication
- PHP External Captive Portal, Controller’s Firewall Friendly API
- Index
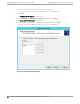
Once Extreme Campus Controller acknowledges the switch configuration, the switch enters the
machine state Running. This state is represented in Extreme Campus Controller with a green circle.
Figure 3: Extreme Campus Controller: Switch States During Discovery
Related Topics
Switch Discovery in an Availability Pair on page 21
Switch Discovery Process on page 19
Switch Discovery in an Availability Pair
When configuring ExtremeXOS switches in an Extreme Campus Controller (Extreme Campus
Controller) Availability Pair, use an "A" record for extremecontrol@<domain-name>, providing
an IP address for the primary Extreme Campus Controller and an IP address for the backup Extreme
Campus Controller. When the first address fails, the switch attempts the second IP address. If both IP
addresses fail, the switch performs a second DNS request. The switch performs the DNS request before
sending an HTTPS message and does not use DNS caching.
• If both the primary and backup Extreme Campus Controller are up, all configured switches are
adopted on the primary Extreme Campus Controller, and the switch sends the HTTPS message to
the primary Extreme Campus Controller only.
• If the primary Extreme Campus Controller is down and the backup Extreme Campus Controller is up,
the switch fails over to the backup. The switch will timeout on the primary IP address and proceed to
the secondary IP address. The switch attempts to send the HTTPS message to the primary Extreme
Campus Controller first because its IP address is first in the DNS reply. That attempt will timeout and
the switch will send the second HTTPS to the secondary IP address. The switch continues to send
HTTPS messages to both IP addresses. If the primary Extreme Campus Controller comes up, the
switch sends the HTTP message to the first IP address and does not attempt the second IP address.
Related Topics
Switch Discovery Process on page 19
Discovering Switches on page 20
Sites
Use sites to define boundaries for fast roaming and session mobility without interruption. A site
represents a physical, geographic area in your network. As the top-level element in the Extreme
Campus Controller data model, the site runs Sessions Manager and RF Manager functions for all RF
Domains in the site.
The following ExtremeWireless™ access points are supported by Extreme Campus Controller:
• AP302W
• AP305C/CX
• AP310i/e
• AP310i-1
• AP360i/e
About Extreme Campus Controller Deployment
Sites
Extreme Campus Controller Deployment Guide for version 5.46.03 21