Deployment Guide
Table Of Contents
- Table of Contents
- Preface
- About Extreme Campus Controller Deployment
- Configuring DHCP, NPS, and DNS Services
- Centralized Site with a Captive Portal
- Centralized Site with AAA Network
- Deploying a Mesh Network
- Configuring an External NAC Server for MBA and AAA Authentication
- Manage RADIUS Servers for User Authentication
- External Captive Portal on a Third-Party Server
- Access Control Rule Admin Portal Access
- Deploying Centralized Web Authentication
- Deploying ExtremeCloud IQ - SE as an External Captive Portal
- Deployment Strategy
- Configuring an External Captive Portal Network
- Editing the Configuration Profile for Network and Roles
- Extreme Campus Controller Default Pass-Through Rule
- Adding Extreme Campus Controller as a Switch to ExtremeCloud IQ - Site Engine
- Editing the Unregistered Policy on ExtremeCloud IQ - Site Engine
- Editing the ExtremeCloud IQ - Site Engine Profile for Policy and Location-Based Services
- Deploying an ExtremeGuest Captive Portal
- Deploying Client Bridge
- Deploying an Availability Pair
- Deploying Universal APs
- Extreme Campus Controller Pair with ExtremeLocation and AirDefense
- ECP Local Authentication
- PHP External Captive Portal, Controller’s Firewall Friendly API
- Index
4. Select Yes to assign the WLAN to desired device groups or SKIP to assign them later.
Editing the Configuration Profile for Network and Roles
Configure a network and be aware of policy roles that you are using before modifying the device group
profile.
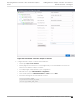
1. On Extreme Campus Controller, go to Configure > Sites and select a site.
2. Select Device Groups tab.
3. Select your configured device group.
4. Beside the Profile field, select
to edit the configuration profile.
5. From the Networks tab, assign a radio to the network you created.
6. From the Roles tab, select the appropriate roles that will be applied to the end system during
connection/registration/authorization. Typically all roles are selected.
Note
Upon creating an External Captive Portal WLAN the Extreme Campus Controller
automatically creates the following internal rule:
• Unregistered role for <network name>
The following are rule examples:
Unregistered role for Guest:acfilters# show
Custom AP Filters: disable
filter 1 3 proto udp eth 800 mac any 0.0.0.0/0 port 53 in dst out src allow
filter 2 3 proto udp eth 800 mac any 0.0.0.0/0 port 67 in dst out src allow
filter 3 3 proto any eth any mac any 0.0.0.0/0 all_ports in none out src allow
filter 4 3 proto icmp eth 800 mac any 0.0.0.0/0 type-code 0x0000 0x0000 in
dst out src allow
filter 5 3 proto tcp eth 800 mac any 1.1.1.1/32 all_ports in dst out src allow
filter 6 3 app-signature group "Web Applications" hostname
"fqdn:nac_engine.mynetwork.com" proto any eth 800 mac any 0.0.0.0/0 all_ports
in dst out src allow
filter 7 3 proto tcp eth 800 mac any 0.0.0.0/0 port 80 in dst out none
redirect
filter 8 3 proto tcp eth 800 mac any 0.0.0.0/0 port 443 in dst out none
redirect
Enabling Captive Portal on a WLAN automatically builds the Unregistered role for
<Network Name> and the necessary rules for client redirection. This role is automatically
assigned to device groups that have the External Captive Portal WLAN selected to
broadcast. Unregistered role for <Network Name> is not visible within the Extreme
Campus Controller user interface. No modification or role creation is necessary for the
functional External Captive Portal environment. Extreme Control must send back the filter-
id of Unregistered role for <Network Name> to use the automatically created role.
7. Select Save to save the Profile settings.
8. Select Close to close the device group.
Extreme Campus Controller Default Pass-Through Rule
Create a RADIUS Pass-Through rule on Extreme Campus Controller. This rule designates that trac
connecting to the Guest network will send and receive all RADIUS requests from the externally defined
RADIUS server, not from the Extreme Campus Controller that processes the request. This includes filter-
ids that are received as attributes. The ExtremeControl RADIUS server provides RADIUS authentication
Deploying ExtremeCloud IQ - SE as an External Captive
Portal Editing the Configuration Profile for Network and Roles
Extreme Campus Controller Deployment Guide for version 5.46.03 155