Deployment Guide
Table Of Contents
- Table of Contents
- Preface
- About Extreme Campus Controller Deployment
- Configuring DHCP, NPS, and DNS Services
- Centralized Site with a Captive Portal
- Centralized Site with AAA Network
- Deploying a Mesh Network
- Configuring an External NAC Server for MBA and AAA Authentication
- Manage RADIUS Servers for User Authentication
- External Captive Portal on a Third-Party Server
- Access Control Rule Admin Portal Access
- Deploying Centralized Web Authentication
- Deploying ExtremeCloud IQ - SE as an External Captive Portal
- Deployment Strategy
- Configuring an External Captive Portal Network
- Editing the Configuration Profile for Network and Roles
- Extreme Campus Controller Default Pass-Through Rule
- Adding Extreme Campus Controller as a Switch to ExtremeCloud IQ - Site Engine
- Editing the Unregistered Policy on ExtremeCloud IQ - Site Engine
- Editing the ExtremeCloud IQ - Site Engine Profile for Policy and Location-Based Services
- Deploying an ExtremeGuest Captive Portal
- Deploying Client Bridge
- Deploying an Availability Pair
- Deploying Universal APs
- Extreme Campus Controller Pair with ExtremeLocation and AirDefense
- ECP Local Authentication
- PHP External Captive Portal, Controller’s Firewall Friendly API
- Index
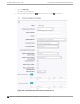
Consecutive failed Authentications
The number of failed authentication attempts. Valid values are 1 to 10. Default value is 5.
Elapsed time for failed Authentications (Seconds)
The threshold in seconds that determines if the client authentication requests are blocked.
This is the window of time in which the failed authentication attempts occur. Valid values are
1 to 10 seconds. The default value is 3 seconds.
Quiet Timeout (Seconds)
The amount of time that authentication requests from the client are blocked before its
RADIUS requests are forwarded to the RADIUS server again. Valid values are 1 to 300
seconds. The default value is 300 seconds (5 minutes).
By default, if 5 attempts are made within 3 seconds, the client authentication requests are
blocked for 300 seconds (5 minutes), and RADIUS requests from that client are ignored. After 5
minutes, client RADIUS requests are forwarded to the RADIUS server again.
Note
In Failover mode, the Deny list is published to the peer Extreme Campus Controller.
Operator Name
RADIUS attribute composed of the operator namespace identifier and the operator name. The
combination of operator name and namespace identifier uniquely identifies the owner of an
access network. The Operator Name cannot exceed 253 bytes. Valid values are:
• Tadig — Three-character Country Code followed by a two- character alphanumeric operator
ID
• Realm — Registered Domain Name of Operator
• E212 — Mobile Country Code or Mobile Network Code
• OneCC — Three-character Country Code followed by 1-6 uppercase ITU Carrier Codes
• None
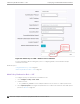
RADIUS Authentication Servers
To add RADIUS servers for authentication, select Add. You can configure up to four RADIUS
servers for authentication.
We have the CWA server configured.
RADIUS Accounting Servers
To add RADIUS servers for accounting, select Add. You can configure up to four RADIUS servers
for accounting.
We have the CWA server configured.
Related Topics
RADIUS Settings on page 127
Deployment Strategy on page 120
CWA Network Settings — ISE on page 127
CWA Policy Redirection Role — ISE on page 130
Configure Authorization Policy on Cisco® ISE Server on page 132
Configure
AAA Policy — ISE Deploying Centralized Web Authentication
126 Extreme Campus Controller Deployment Guide for version 5.46.03