Deployment Guide
Table Of Contents
- Table of Contents
- Preface
- About Extreme Campus Controller Deployment
- Configuring DHCP, NPS, and DNS Services
- Centralized Site with a Captive Portal
- Centralized Site with AAA Network
- Deploying a Mesh Network
- Configuring an External NAC Server for MBA and AAA Authentication
- Manage RADIUS Servers for User Authentication
- External Captive Portal on a Third-Party Server
- Access Control Rule Admin Portal Access
- Deploying Centralized Web Authentication
- Deploying ExtremeCloud IQ - SE as an External Captive Portal
- Deployment Strategy
- Configuring an External Captive Portal Network
- Editing the Configuration Profile for Network and Roles
- Extreme Campus Controller Default Pass-Through Rule
- Adding Extreme Campus Controller as a Switch to ExtremeCloud IQ - Site Engine
- Editing the Unregistered Policy on ExtremeCloud IQ - Site Engine
- Editing the ExtremeCloud IQ - Site Engine Profile for Policy and Location-Based Services
- Deploying an ExtremeGuest Captive Portal
- Deploying Client Bridge
- Deploying an Availability Pair
- Deploying Universal APs
- Extreme Campus Controller Pair with ExtremeLocation and AirDefense
- ECP Local Authentication
- PHP External Captive Portal, Controller’s Firewall Friendly API
- Index
For controllers in an availability pair, the primary and backup servers must be synchronized
when the WLAN Services are synchronized. If the primary server has failed resulting in a
backup server being used for authentication, the controller periodically sends a "Health
Check" to the primary server to see if it has recovered. If the primary server has recovered,
the controller starts using the primary server for all new authentications. All authentications
in progress continue to use the backup server.
Note
There is no correlation between the RADIUS server that is used for authentication and
the RADIUS server that is used for accounting.
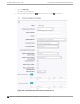
Include Framed IP
Select this option to include the FRAMED-IP attribute value pair in the RADIUS ACCESS-REQ
message. You can include the user IP address in the RADIUS ACCESS-REQ through the
FRAMED-IP attribute. This can extend user access reporting capabilities. Framed IP is supported
by External Captive Portal only. Centralized Web Authentication does not support Framed IP.
Report NAS Location
Sends Network Access Server (NAS) Location per the RFC5580 Out of Band agreement. After a
NAS Location change, the new NAS Location is reported in the next RADIUS Request or RADIUS
Accounting message.
Note
Mid-session requests and the Initial Server Request for Location as described in
RFC5580 are not supported.
The following additional attributes (AVP) used by RFC5580 are supported:
• LOCATION-INFO
• LOCATION-DATA
Note
Site Location details are reported in LOCATION-DATA. For more information on Site
Location information, see the Users Guide.
• BASIC-LOCATION-POLICY-RULES
• OPERATOR-NAME (Described below)
Block repeated failed Authentications
Enable this setting to minimize the RADIUS server load that is created by repeated
authentication requests and failures. Authentication requests from a client are blocked for a
configurable period of time. While blocked, RADIUS requests from the client are ignored. This
setting applies to a specific WLAN. The client can continue to send authentication requests on a
dierent WLAN.
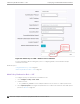
Consecutive failed Authentications must be received at the Extreme Campus Controller in the
Elapsed time for failed Authentications (Seconds) for the Quiet Timeout (Seconds) to start.
After the quiet timeout expires, the client’s RADIUS requests are forwarded to the RADIUS
server again.
When enabled, the following settings display:
Deploying Centralized Web Authentication
Configure AAA Policy — ISE
Extreme Campus Controller Deployment Guide for version 5.46.03 125