Installation manual
Table Of Contents
- Introduction
- Terminology and abbreviations
- System requirements
- Installation
- Architecture Overview
- Integration with Email Messaging System
- Important ESET Mail Security mechanisms
- ESET Security system update
- Let us know
- Appendix A. ESETS setup and configuration
- Setting ESETS for MTA Postfix
- Setting ESETS for MTA Sendmail
- Setting ESETS for MTA Qmail
- Setting ESETS for MTA Exim version 3
- Setting ESETS for MTA Exim version 4
- Setting ESETS for MTA ZMailer
- Setting ESETS for MTA Novell GroupWise
- Setting ESETS for outbound email message scanning
- Setting ESETS for scanning of POP3 communication
- Setting ESETS for scanning of IMAP communication
- Appendix B. PHP License
16
7. Important ESET Mail Security mechanisms
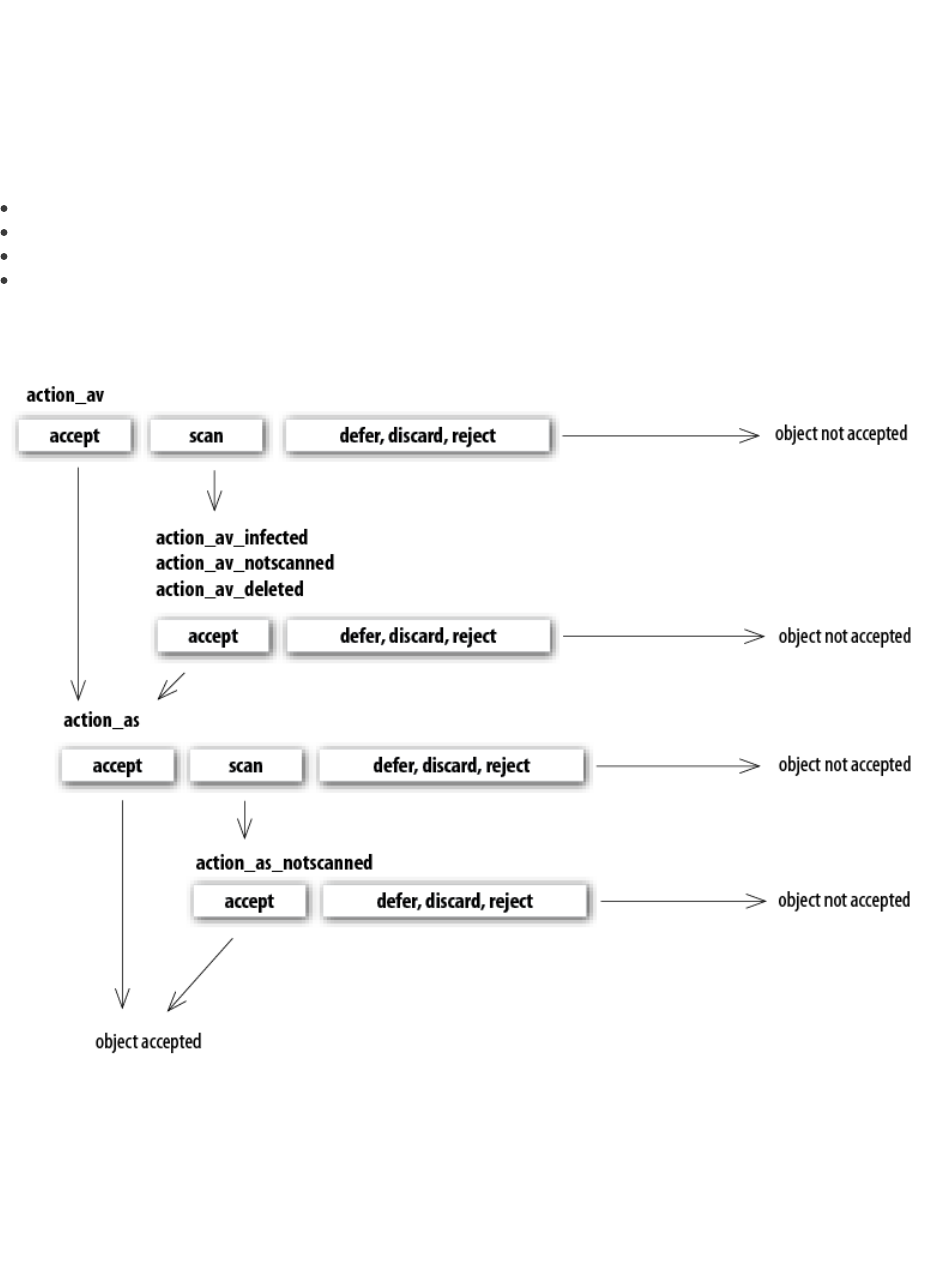
7.1 Handle Object Policy
The Handle Object Policy (see figure 6-1) mechanism provides filtering for scanned objects based on their status. This
functionality is based on the following configuration options:
action_av
action_av_infected
action_av_notscanned
action_av_deleted
For detailed information on these options, please refer to the esets.cfg(5) man page.
Figure 6-1. Scheme of Handle Object Policy mechanism.
Every processed object is first handled according to the configuration of the ‘action_av‘ option. If this option is set to ‘accept’ (or
‘defer’, ‘discard’, ‘reject’) the object is accepted (or deferred, discarded, rejected). If the option is set to ‘scan’ the object is scanned
for virus infiltrations, and if the ‘av_clean_mode’ option is set to ‘yes’, the object is also cleaned. In addition, the configuration
options ‘action_av_infected’, ‘action_av_notscanned’ and ‘action_av_deleted’ are taken into account to further evaluate object
handling. If an ‘accept’ action has been taken as a result of these three action options, the object is accepted. Otherwise, the
object is blocked.
7.2 User Specific Configuration
The purpose of the User Specific Configuration mechanism is to provide a higher degree of customization and functionality. It
allows the system administrator to define ESETS antivirus scanner parameters based on the user who is accessing file system
objects.
A detailed description of this functionality can be found in the esets.cfg(5) man page. In this section we will provide only a short
example of a user-specific configuration.
Here, the esets_smtp module is used as a content filter for MTA Postfix. The functionality of this module is based on the [smtp]
section in the ESETS configuration file (esets.cfg). See below: