Installation manual
Table Of Contents
- Introduction
- Terminology and abbreviations
- System requirements
- Installation
- Architecture Overview
- Integration with Email Messaging System
- Important ESET Mail Security mechanisms
- ESET Security system update
- Let us know
- Appendix A. ESETS setup and configuration
- Setting ESETS for MTA Postfix
- Setting ESETS for MTA Sendmail
- Setting ESETS for MTA Qmail
- Setting ESETS for MTA Exim version 3
- Setting ESETS for MTA Exim version 4
- Setting ESETS for MTA ZMailer
- Setting ESETS for MTA Novell GroupWise
- Setting ESETS for outbound email message scanning
- Setting ESETS for scanning of POP3 communication
- Setting ESETS for scanning of IMAP communication
- Appendix B. PHP License
15
6.5.3 Scanning email messages using Novell GroupWise
Novell GroupWise is a messaging and collaborative software platform that also supports email management. The platform
consists of the client and server software, available for various platforms (i.e. Linux).
The module esets_gwia only allows the scanning of incoming email messages. For delivering email messages to clients
immediately, the following GroupWise agent directories must have set the same paths:
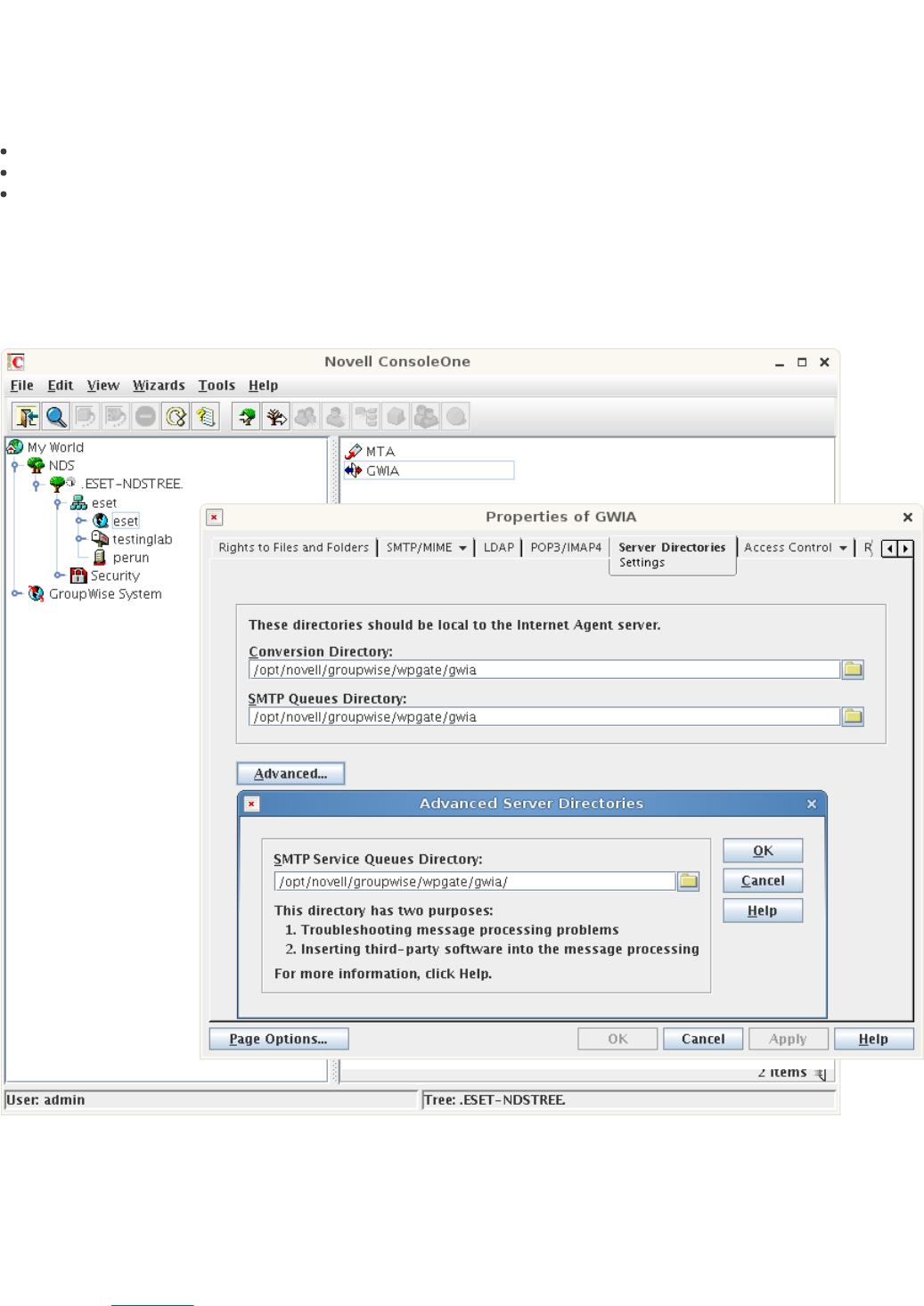
Conversion Directory
SMTP Queues Directory
SMTP Service Queues Directory
To perform this, open the Novell ConsoleOne, navigate to NDS > ESET-NDSTREE > eset > domain > GWIA > Propertiers > Server
Directories Settings and set the particular parameters. There is an example domain called eset featured in our case. Then restart
the GroupWise agent:
/etc/init.d/grpwise restart
Figure 5-4. Novell ConcoleOne module settings.
To configure ESET Mail Security to scan email messages downloaded from Novell GroupWise server, run the following script:
@SBINDIR@/esets_setup
Select the MTA install option. This will configure the GWIA (Novell GroupWise Internet Agent) and the esets_gwia module
parameters and directories, where email queues (files) are being scanned and watched.
Note that the installer is performing a backup of all modified configuration files and can display every command that it will
execute after your approval. The backup configuration files should be reimplemented after uninstalling. Detailed configuration
is described in appendix A of this documentation.