Installation manual
62
Block communication that uses the certificate – Terminates connection to the site that uses the certificate.
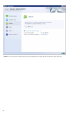
4.1.6.1.1 Trusted certificates
In addition to the integrated Trusted Root Certification Authorities store where ESET Mail Security stores trusted
certificates, you can create a custom list of trusted certificates that can be viewed in Advanced Setup (F5) >
Protocol filtering > SSL > Certificates > Trusted certificates.
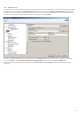
4.1.6.1.2 Excluded certificates
The Excluded certificates section contains certificates that are considered safe. The content of encrypted
communications utilizing the certificates in the list will not be checked for threats. We recommend excluding only
those web certificates that are guaranteed to be safe and the communication utilizing the certificates does not
need to be checked.
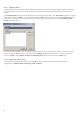
4.1.7 ThreatSense engine parameters setup
ThreatSense is the name of the technology consisting of complex threat detection methods. This technology is
proactive, which means it also provides protection during the early hours of the spread of a new threat. It uses a
combination of several methods (code analysis, code emulation, generic signatures, virus signatures) which work
in concert to significantly enhance system security. The scanning engine is capable of controlling several data
streams simultaneously, maximizing the efficiency and detection rate. ThreatSense technology also successfully
eliminates rootkits.
The ThreatSense technology setup options allow you to specify several scan parameters:
File types and extensions that are to be scanned
The combination of various detection methods
Levels of cleaning, etc.
To enter the setup window, click the Setup... button located in any module‘s setup window which uses
ThreatSense technology (see below). Different security scenarios could require different configurations. With this in
mind, ThreatSense is individually configurable for the following protection modules:
Real-time file system protection
System startup file check
Email protection
Web access protection
On-demand computer scan
The ThreatSense parameters are highly optimized for each module, and their modification can significantly
influence system operation. For example, changing parameters to always scan runtime packers, or enabling
advanced heuristics in the real-time file system protection module could result in a system slow-down (normally,
only newly-created files are scanned using these methods). Therefore, we recommend that you leave the default
ThreatSense parameters unchanged for all modules except On-demand computer scan.
48
51
55
58