Installation manual
95
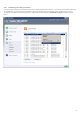
Greylisting
All messages that have been evaluated using the greylisting method are recorded in this log.
Columns description:
Time – time of entry into the antispam log
HELO Domain – domain name used by the sending server to identify itself towards the receiving server
IP address – sender's IP address
Sender – sender's address
Recipient – recipient's address
Action – may contain the following statuses:
Rejected
The incoming message was denied using the basic precept of greylisting (first
delivery attempt)
Rejected (not verified)
The incoming message was redelivered by the sending server, but the time limit to
deny the connection has not elapsed yet (Time limit for the initial connection
denial).
Verified
The incoming message was redelivered several times by the sending server, the
Time limit for the initial connection denial has elapsed and the message was
successfully verified and delivered. See also Transport agent .
Time remaining – the time left until the Time limit for the initial connection denial will be met
Detected threats
Threat log offers detailed information about infiltrations detected by ESET Mail Security modules. The information
includes the time of detection, scanner type, object type, object name, infiltration name, location, the performed
action and the name of the user logged in at the time the infiltration was detected. To copy or delete one or more
lines from the log (or to delete the whole log), use the context menu (right-click on the item).
Events
The Event log contains information about events and errors that have occurred in the program. Often the
information found here can help you find a solution for a problem occurring in the program.
36