Installation manual
76
4.1.7.5 Limits
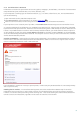
The Limits section allows you to specify the maximum size of objects and levels of nested archives to be scanned:
Maximum object size: – Defines the maximum size of objects to be scanned. The given antivirus module will then
scan only objects smaller than the size specified. We do not recommend changing the default value, as there is
usually no reason to modify it. This option should only be changed by advanced users who have specific reasons for
excluding larger objects from scanning.
Maximum scan time for object (sec.): – Defines the maximum time value for scanning an object. If a user-defined
value has been entered here, the antivirus module will stop scanning an object when that time has elapsed,
regardless of whether the scan has finished.
Archive nesting level: –Specifies the maximum depth of archive scanning. We do not recommend changing the
default value of 10; under normal circumstances, there should be no reason to modify it. If scanning is prematurely
terminated due to the number of nested archives, the archive will remain unchecked.
Maximum size of file in archive: – This option allows you to specify the maximum file size for files contained in
archives (when they are extracted) that are to be scanned. If this causes scanning an archive to be prematurely
terminated, the archive will remain unchecked.
NOTE: When a blue dot is shown next to a parameter, it means that current setting for this parameter differ from
setting for other modules that also use ThreatSense. Since you can configure the same parameter differently for
each module, this blue dot only reminds you that this same parameter is configured differently for other modules. If
there isn't a blue dot, parameter for all the modules is configured the same way.
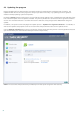
4.1.7.6 Other
Scan alternate data streams (ADS) – Alternate data streams (ADS) used by the NTFS file system are file and folder
associations which are invisible from ordinary scanning techniques. Many infiltrations try to avoid detection by
disguising themselves as alternative data streams.
Run background scans with low priority – Each scanning sequence consumes a certain amount of system
resources. If you work with programs that place a high load on system resources, you can activate low priority
background scanning and save resources for your applications.
Log all objects – If this option is selected, the log file will show all the scanned files, even those not infected.
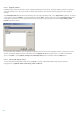
Enable Smart optimization – Select this option so that files which have already been scanned are not scanned
repeatedly (unless they have been modified). Files are scanned again immediately after each virus signature
database update.
Preserve last access timestamp – Select this option to keep the original access time of scanned files instead of
updating it (e.g., for use with data backup systems).
Scroll log – This option allows you to enable/disable log scrolling. If selected, information scrolls upwards within
the display window.
Display notification about scan completion in a separate window – Opens a standalone window containing
information about scan results.
NOTE: When a blue dot is shown next to a parameter, it means that current setting for this parameter differ from
setting for other modules that also use ThreatSense. Since you can configure the same parameter differently for
each module, this blue dot only reminds you that this same parameter is configured differently for other modules. If
there isn't a blue dot, parameter for all the modules is configured the same way.