Installation manual
73
4.1.7.1 Objects setup
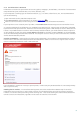
The Objects section allows you to define which computer components and files will be scanned for infiltrations.
Operating memory – Scans for threats that attack the operating memory of the system.
Boot sectors – Scans boot sectors for the presence of viruses in the master boot record.
Files – Provides scanning for all common file types (programs, pictures, audio, video files, database files, etc.).
Email files – Scans special files where email messages are contained.
Archives – Provides scanning for files compressed in archives (.rar, .zip, .arj, .tar, etc.).
Self-extracting archives – Scans files which are contained in self-extracting archive files, but typically presented
with an .exe file extension
Runtime packers – Runtime packers (unlike standard archive types) decompress in memory, in addition to
standard static packers (UPX, yoda, ASPack, FGS, etc.).
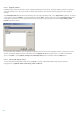
NOTE: When a blue dot is shown next to a parameter, it means that current setting for this parameter differ from
setting for other modules that also use ThreatSense. Since you can configure the same parameter differently for
each module, this blue dot only reminds you that this same parameter is configured differently for other modules. If
there isn't a blue dot, parameter for all the modules is configured the same way.
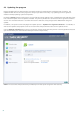
4.1.7.2 Options
In the Options section, you can select the methods to be used when scanning the system for infiltrations. The
following options are available:
Signatures – Signatures can exactly and reliably detect and identify infiltrations by their name using virus
signatures.
Heuristics – Heuristics use an algorithm that analyses the (malicious) activity of programs. The main advantage of
heuristic detection is the ability to detect new malicious software which did not previously exist, or was not
included in the list of known viruses (virus signatures database).
Advanced heuristics – Advanced heuristics comprise a unique heuristic algorithm, developed by ESET, optimized
for detecting computer worms and trojan horses written in high-level programming languages. Due to advanced
heuristics, the detection intelligence of the program is significantly higher.
Adware/Spyware/Riskware – This category includes software which collects various sensitive information about
users without their informed consent. This category also includes software which displays advertising material.
Potentially unwanted applications – Potentially unwanted applications are not necessarily intended to be
malicious, but may affect the performance of your computer in a negative way. Such applications usually require