Operator`s manual
INTRODUCTION
1-2
June 1997
Part No. 002-0690-201
1.4 STARTING THE PROGRAM
1. Turn on the computer and monitor. The computer
will boot up and display a Welcome window.
2. Press Ctrl+Alt+Del to log on. Another Welcome
window displays.
3. Verify username, enter password, and press return.
The HP OpenView log-in window displays.
4. Choose Operator security level, enter the password,
and press return. The OpenView application starts,
displays its menus, and displays a Home map of the
network system.
OpenView is in the startup group and will auto-
matically start when the computer is turned on. To
start OpenView while Windows NT is running, the
OpenView application is stored in the OpenView Pro-
gram Group of the Program Manager.
1.5 OVERVIEW OF MANAGING AN E.F.
JOHNSON NETWORK
An E.F. Johnson Network is a system that enables
remote repeater sites to report significant events to a
host computer, where the events can be managed. The
host computer runs the HP OpenView program and an
E.F. Johnson proprietary application, which together
use alarms to report significant events. The alarms are
reported to the screen of the host computer by chang-
ing the color of map icons and by displaying an entry
in an alarm log. The operator can then decide how to
respond to the alarms. In addition, the system can be
configured to automatically manage some alarms.
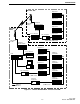
Figure 1-1 shows a typical central and remote
site. There may be several other remote sites of similar
configuration.
The remote sites communicate to the host com-
puter (often located at the central site) via DS0 links
(64 K bps). In this diagram, the DS0 link is part of the
microwave link that carries other information between
sites. Within a site, network components capable of
TCP/IP are connected with 10BaseT Ethernet®. The
site/channel computers are also connected by a serial
link to MBCs (Message Bridge Cards) in the repeaters
and channel controllers. E.F. Johnson proprietary soft-
ware is used to communicate between the computer
and MBC; then, the computers pass the information
via TCP/IP to the host computer.
Alarms arrive at the host computer through sev-
eral means. Computers and routers can be polled by
the host computer on a regular basis to determine if the
network link is functioning. Routers will send SNMP
(Simple Network Management Protocol) trap mes-
sages to the host computer when a significant event
occurs. The E.F. Johnson proprietary software will
send messages to the host computer when significant
events occur in repeaters and channel controllers.
Repeaters and channel controllers also have IACs
(Interface Alarm Cards) that can report external
alarms, such as open doors. These alarms are also
reported through the E.F. Johnson proprietary soft-
ware.
Some alarms will correct themselves. For exam-
ple, if a door opens, an alarm will be received that the
door is open. When the door closes, an alarm will be
received that the door has closed.
Some alarms can be configured to be managed
automatically by the system. These are called Reverts.
For example, if a critical alarm reports that one
repeater is not working, the system could be config-
ured to automatically shut down all repeaters on that
channel. The problem is not corrected, but it is man-
aged. It is not a perfect solution, but it may be the best
solution for the circumstances. The critical alarm still
exists, in fact more of them exist because more repeat-
ers are not working. However, the system may be
more useful without one channel, than with a large
hole in the coverage of one channel.
Other alarms will have to be handled manually. If
a door opens but does not close and no one is supposed
to be at the site, the police may need to be called to go
see who is there. If a storm takes out an entire site,
some major work will need to be done.