Concept Guide
Table Of Contents
- About this Guide
- About Instant
- Setting up a W-IAP
- Automatic Retrieval of Configuration
- Instant User Interface
- Initial Configuration Tasks
- Customizing W-IAP Settings
- Modifying the W-IAP Host Name
- Configuring Zone Settings on a W-IAP
- Specifying a Method for Obtaining IP Address
- Configuring External Antenna
- Configuring Radio Profiles for a W-IAP
- Configuring Uplink VLAN for a W-IAP
- Changing the W-IAP Installation Mode
- Changing USB Port Status
- Master Election and Virtual Controller
- Adding a W-IAP to the Network
- Removing a W-IAP from the Network
- VLAN Configuration
- IPv6 Support
- Wireless Network Profiles
- Configuring Wireless Network Profiles
- Configuring Fast Roaming for Wireless Clients
- Configuring Modulation Rates on a WLAN SSID
- Multi-User-MIMO
- Management Frame Protection
- Disabling Short Preamble for Wireless Client
- Editing Status of a WLAN SSID Profile
- Editing a WLAN SSID Profile
- Deleting a WLAN SSID Profile
- Wired Profiles
- Captive Portal for Guest Access
- Understanding Captive Portal
- Configuring a WLAN SSID for Guest Access
- Configuring Wired Profile for Guest Access
- Configuring Internal Captive Portal for Guest Network
- Configuring External Captive Portal for a Guest Network
- Configuring Facebook Login
- Configuring Guest Logon Role and Access Rules for Guest Users
- Configuring Captive Portal Roles for an SSID
- Configuring Walled Garden Access
- Authentication and User Management
- Managing W-IAP Users
- Supported Authentication Methods
- Supported EAP Authentication Frameworks
- Configuring Authentication Servers
- Understanding Encryption Types
- Configuring Authentication Survivability
- Configuring 802.1X Authentication for a Network Profile
- Enabling 802.1X Supplicant Support
- Configuring MAC Authentication for a Network Profile
- Configuring MAC Authentication with 802.1X Authentication
- Configuring MAC Authentication with Captive Portal Authentication
- Configuring WISPr Authentication
- Blacklisting Clients
- Uploading Certificates
- Roles and Policies
- DHCP Configuration
- Configuring Time-Based Services
- Dynamic DNS Registration
- VPN Configuration
- IAP-VPN Deployment
- Adaptive Radio Management
- Deep Packet Inspection and Application Visibility
- Voice and Video
- Services
- Configuring AirGroup
- Configuring a W-IAP for RTLS Support
- Configuring a W-IAP for Analytics and Location Engine Support
- Managing BLE Beacons
- Clarity Live
- Configuring OpenDNS Credentials
- Integrating a W-IAP with Palo Alto Networks Firewall
- Integrating a W-IAP with an XML API Interface
- CALEA Integration and Lawful Intercept Compliance
- Cluster Security
- W-IAP Management and Monitoring
- Uplink Configuration
- Intrusion Detection
- Mesh W-IAP Configuration
- Mobility and Client Management
- Spectrum Monitor
- W-IAP Maintenance
- Monitoring Devices and Logs
- Hotspot Profiles
- ClearPass Guest Setup
- IAP-VPN Deployment Scenarios
- Acronyms and Abbreviations
Dell Networking W-Series Instant 6.5.1.0-4.3.1.0 | User Guide Intrusion Detection | 328
Chapter 27
Intrusion Detection
The Intrusion Detection System (IDS) is a feature that monitors the network for the presence of unauthorized
W-IAPs and clients. It also logs information about the unauthorized W-IAPs and clients, and generates reports
based on the logged information.
The IDS feature in the Instant network enables you to detect rogue W-IAPs, interfering W-IAPs, and other
devices that can potentially disrupt network operations.
This chapter describes the following procedures:
l Detecting and Classifying Rogue W-IAPs on page 328
l OS Fingerprinting on page 328
l Configuring Wireless Intrusion Protection and Detection Levels on page 329
l Configuring IDS on page 334
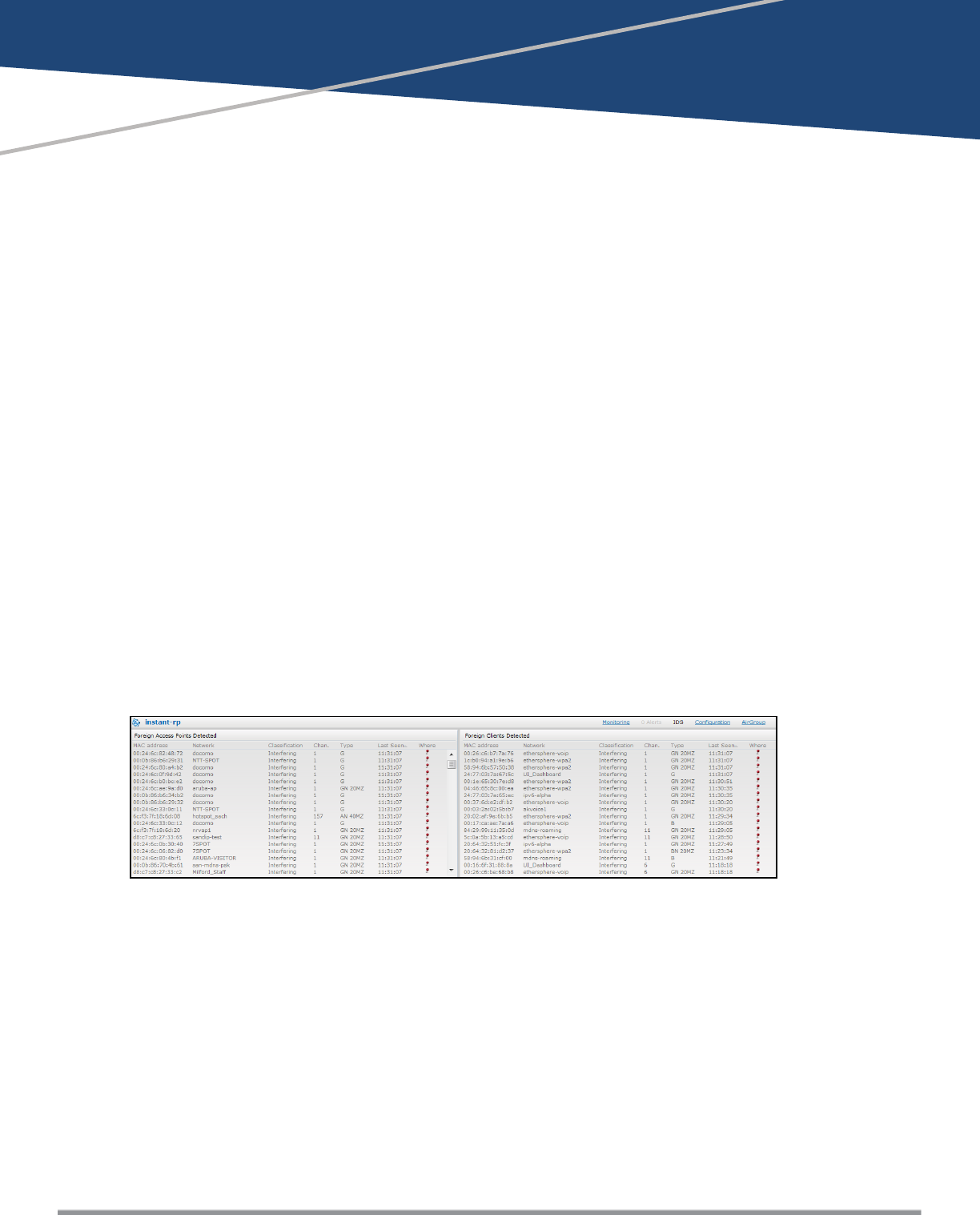
Detecting and Classifying Rogue W-IAPs
A rogue W-IAP is an unauthorized W-IAP plugged into the wired side of the network.
An interfering W-IAP is an W-IAP seen in the RF environment but it is not connected to the wired network. While
the interfering W-IAP can potentially cause RF interference, it is not considered a direct security threat, because
it is not connected to the wired network. However, an interfering W-IAP may be reclassified as a rogue W-IAP.
To detect the rogue W-IAPs, click the IDS link in the Instant main window. The built-in IDS scans for access
points that are not controlled by the VC. These are listed and classified as either Interfering or Rogue,
depending on whether they are on a foreign network or your network.
Figure 95 Intrusion Detection
OS Fingerprinting
The OS Fingerprinting feature gathers information about the client that is connected to the Instant network to
find the operating system that the client is running on. The following is a list of advantages of this feature:
l Identifying rogue clients—Helps to identify clients that are running on forbidden operating systems.
l Identifying outdated operating systems—Helps to locate outdated and unexpected OS in the company
network.
l Locating and patching vulnerable operating systems—Assists in locating and patching specific operating
system versions on the network that have known vulnerabilities, thereby securing the company network.
OS Fingerprinting is enabled in the Instant network by default. The following operating systems are identified
by Instant:










