Concept Guide
Table Of Contents
- About this Guide
- About Instant
- Setting up a W-IAP
- Automatic Retrieval of Configuration
- Instant User Interface
- Initial Configuration Tasks
- Customizing W-IAP Settings
- Modifying the W-IAP Host Name
- Configuring Zone Settings on a W-IAP
- Specifying a Method for Obtaining IP Address
- Configuring External Antenna
- Configuring Radio Profiles for a W-IAP
- Configuring Uplink VLAN for a W-IAP
- Changing the W-IAP Installation Mode
- Changing USB Port Status
- Master Election and Virtual Controller
- Adding a W-IAP to the Network
- Removing a W-IAP from the Network
- VLAN Configuration
- IPv6 Support
- Wireless Network Profiles
- Configuring Wireless Network Profiles
- Configuring Fast Roaming for Wireless Clients
- Configuring Modulation Rates on a WLAN SSID
- Multi-User-MIMO
- Management Frame Protection
- Disabling Short Preamble for Wireless Client
- Editing Status of a WLAN SSID Profile
- Editing a WLAN SSID Profile
- Deleting a WLAN SSID Profile
- Wired Profiles
- Captive Portal for Guest Access
- Understanding Captive Portal
- Configuring a WLAN SSID for Guest Access
- Configuring Wired Profile for Guest Access
- Configuring Internal Captive Portal for Guest Network
- Configuring External Captive Portal for a Guest Network
- Configuring Facebook Login
- Configuring Guest Logon Role and Access Rules for Guest Users
- Configuring Captive Portal Roles for an SSID
- Configuring Walled Garden Access
- Authentication and User Management
- Managing W-IAP Users
- Supported Authentication Methods
- Supported EAP Authentication Frameworks
- Configuring Authentication Servers
- Understanding Encryption Types
- Configuring Authentication Survivability
- Configuring 802.1X Authentication for a Network Profile
- Enabling 802.1X Supplicant Support
- Configuring MAC Authentication for a Network Profile
- Configuring MAC Authentication with 802.1X Authentication
- Configuring MAC Authentication with Captive Portal Authentication
- Configuring WISPr Authentication
- Blacklisting Clients
- Uploading Certificates
- Roles and Policies
- DHCP Configuration
- Configuring Time-Based Services
- Dynamic DNS Registration
- VPN Configuration
- IAP-VPN Deployment
- Adaptive Radio Management
- Deep Packet Inspection and Application Visibility
- Voice and Video
- Services
- Configuring AirGroup
- Configuring a W-IAP for RTLS Support
- Configuring a W-IAP for Analytics and Location Engine Support
- Managing BLE Beacons
- Clarity Live
- Configuring OpenDNS Credentials
- Integrating a W-IAP with Palo Alto Networks Firewall
- Integrating a W-IAP with an XML API Interface
- CALEA Integration and Lawful Intercept Compliance
- Cluster Security
- W-IAP Management and Monitoring
- Uplink Configuration
- Intrusion Detection
- Mesh W-IAP Configuration
- Mobility and Client Management
- Spectrum Monitor
- W-IAP Maintenance
- Monitoring Devices and Logs
- Hotspot Profiles
- ClearPass Guest Setup
- IAP-VPN Deployment Scenarios
- Acronyms and Abbreviations
(Instant AP)(wired ap profile <name>)# set-role <attribute>{{equals|not-equal|starts-with|
ends-with|contains}<operator> <role>|value-of}
(Instant AP)(wired ap profile <name>)# end
(Instant AP)# commit apply
Example
(Instant AP)(config)# wlan ssid-profile Profile1
(Instant AP)(SSID Profile "Profile1")# set-role mac-address-and-dhcp-options matches-regular-
expression \bring\b Profile1
(Instant AP)(SSID Profile"Profile1")# end
(Instant AP)# commit apply
Understanding VLAN Assignment
You can assign VLANs to a client based on the following configuration conditions:
l The default VLAN configured for the WLAN can be assigned to a client.
l If VLANs are configured for a WLAN SSID or an Ethernet port profile, the VLAN for the client can be derived
before the authentication, from the rules configured for these profiles.
l If a rule derives a specific VLAN, it is prioritized over the user roles that may have a VLAN configured.
l The user VLANs can be derived from the default roles configured for 802.1X authentication or MAC
authentication.
l After client authentication, the VLAN can be derived from Vendor-Specific Attributes (VSA) for RADIUS
server authentication.
l The DHCP-based VLANs can be derived for captive portal authentication.
Instant supports role derivation based on the DHCP option for captive portal authentication. When the
captive portal authentication is successful, the role derivation based on the DHCP option assigns a new user
role to the guest users, instead of the pre-authenticated role.
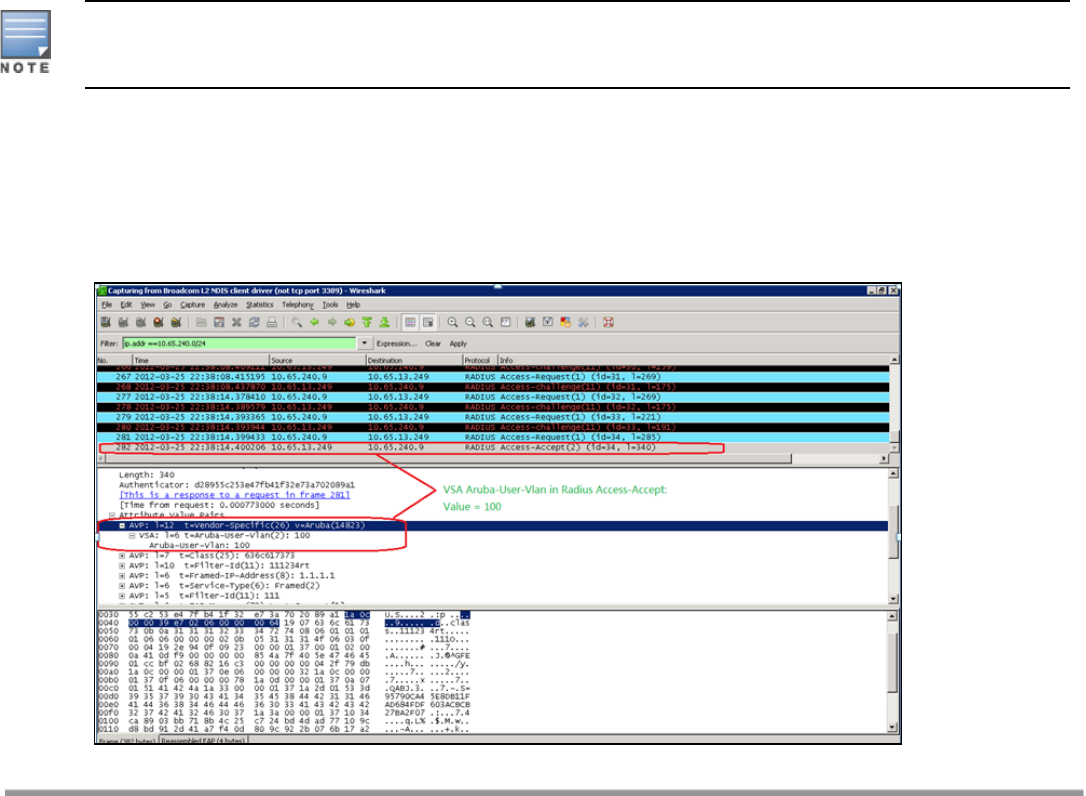
Vendor-Specific Attributes
When an external RADIUS server is used, the user VLAN can be derived from the Dell-User-Vlan VSA. The VSA
is then carried in an Access-Accept packet from the RADIUS server. The W-IAP can analyze the return message
and derive the value of the VLAN which it assigns to the user.
Figure 45 RADIUS Access-Accept Packets with VSA
Dell Networking W-Series Instant 6.5.1.0-4.3.1.0 | User Guide Roles and Policies | 200










