Reference Guide
Table Of Contents
- OpenManage Integration for VMware vCenter version 5.3 Security Configuration Guide
- Figures
- Tables
- PREFACE
- Terms used in this document
- Deployment models
- Product and Subsystem Security
- Security controls map
- Authentication
- Login security settings
- Authentication types and setup considerations
- User and credential management
- Network security
- Data security
- Cryptography
- Auditing and logging
- Serviceability
- OMIVV OS update
- Product code integrity
- Miscellaneous Configuration and Management
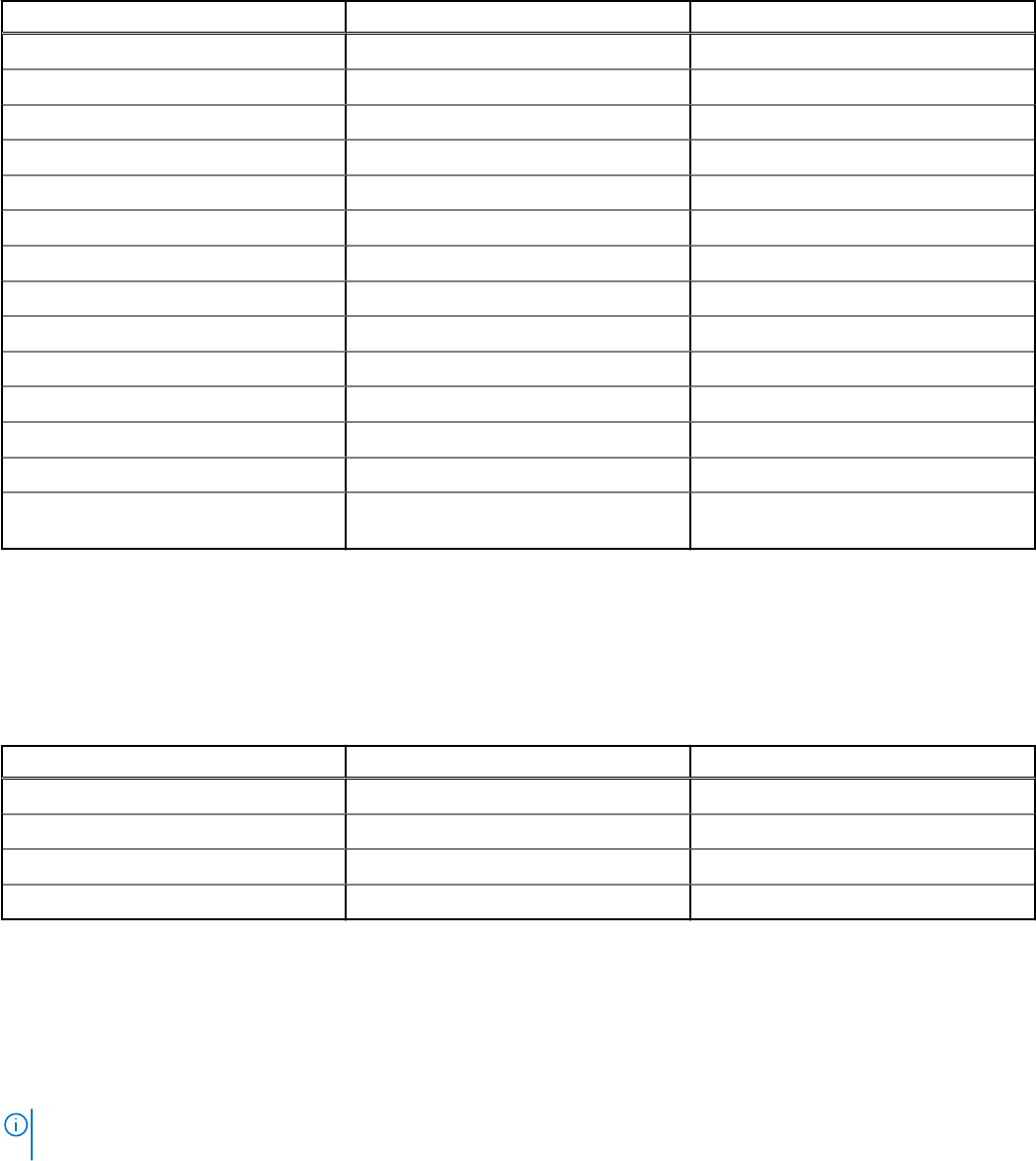
Table 6. Outbound ports
Port number Layer 4 Protocol Service
443 TCP HTTPS
448 TCP Data Protection Search Admin REST API
464 TCP, UDP Kerberos
514 TCP, UDP rsh
587 TCP SMTP
636 TCP, UDP LDAPS
902 TCP VMware ESXi
2049 TCP, UDP NFS
2052 TCP, UDP mountd, clearvisn
3009 TCP Data Domain REST API
5672 TCP RabbitMQ over amqp
8443 TCP MCSDK 8443 is an alternative for 443
9002 TCP Data Protection Advisor REST API
9443 TCP Avamar Management Console web
service
Inbound ports
The inbound ports that are available to be used by a remote system when connecting to OMIVV.
The ports that are listed in the following table are the OMIVV inbound ports.
Table 7. Inbound ports
Port number Layer 4 Protocol Service
22 TCP SSH
80 TCP HTTP
443 TCP HTTPS
5671 TCP RabbitMQ over amqp
Data security
The data that is maintained by OMIVV is stored and secured in internal databases within the appliance and it cannot be
accessed from outside.
The data that is in transit through OMIVV is secured by secure communication channel.
NOTE:
It is recommended that RESTful API users store credentials and data retrieved securely as per your environment
restrictions.
Cryptography
OMIVV uses cryptography for the following components:
● Access control
● Authentication
20
Product and Subsystem Security










