Developers Guide
Server configuration
26 Dell EMC SC Series with Red Hat Enterprise Linux 7x | CML1071
Note: It is no longer recommended to manually edit the /boot/grub/grub.cfg file. Use the grubby command
line interface to achieve boot-level configuration changes. The grubby tool manual pages and help are
available with the following commands, respectively: man grubby or grubby --help.
3.2 iSCSI
RHEL 7.x introduces an updated software implementation of the open-iSCSI stack (based on RFC3720). This
new iSCSI stack resides in the kernel memory space instead of user space.
iSCSI is mature technology that allows organizations to scale into the realm of enterprise storage while
leveraging their existing infrastructure. This section discusses the configuration, use, and implementation of
the open-iSCSI stack only. For more advanced implementations of iSCSI software (which may include custom
iSCSI HBA drivers and offload engines), consult with the associated vendor documentation.
3.2.1 Configuration
The Linux host being configured requires an Ethernet port that can communicate with the iSCSI ports on the
SC Series storage. It is recommend that a dedicated port/VLAN is used for this purpose.
One of the more important considerations when configuring iSCSI is the network path. Due consideration is
recommended to determine the confidentiality, security, and latency required for the iSCSI traffic. These
needs will define and determine the network topology of the iSCSI architecture (such as dedicated physical
ports or VLAN, multipath, and redundancy).
In an ideal scenario, iSCSI traffic is separated and isolated from routine network traffic by the use of
dedicated ports, switches, and infrastructure. If the physical topology is constrained, it is recommended to
separate and isolate iSCSI traffic by the use of VLAN subnets. It is also recommended to always use iSCSI in
a multipath configuration to create path redundancy.
If VLAN subnets are not possible, two further options should be explored:
Route traffic at the network layer by defining static routes.
Route traffic at the iSCSI level through configuration.
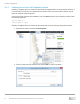
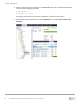
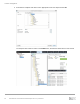
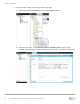
The following demonstration walks through the process of requesting targets from the SC Series storage
discovery IP from the Linux host, logging in to these targets, and setting up an iSCSI-based server object on
the SC Series storage. Additional methods, like scanning for newly discovered volumes, are discussed in
section 2.1.