Deployment Guide
Table Of Contents
- Dell Encryption Personal Installation Guide v11.1
- Contents
- Overview
- Requirements
- Download the Software
- Installation
- Advanced Authentication and Encryption Personal Setup Wizards
- Configure Console Settings
- Uninstall the Master Installer
- Uninstall Using the Child Installers
- Data Security Uninstaller
- Policies and Template Descriptions
- Policies
- Template Descriptions
- Aggressive Protection for All Fixed Drives and External Drives
- PCI Regulation Targeted
- Data Breach Regulation Targeted
- HIPAA Regulation Targeted
- Basic Protection for All Fixed Drives and External Drives (Default)
- Basic Protection for All Fixed Drives
- Basic Protection for System Drive Only
- Basic Protection for External Drives
- Encryption Disabled
- Extract Child Installers
- Troubleshooting
- Glossary
● Set EMS Exclude CD/DVD Encryption = not selected.
● Set Subclass Storage: Optical Drive Control = UDF Only.
Use WSScan
● WSScan allows you to ensure that all data is decrypted when uninstalling Encryption as well as view encryption status and
identify unencrypted files that should be encrypted.
● Administrator privileges are required to run this utility.
NOTE: WSScan must be run in System Mode with the PsExec tool if a target file is owned by the system account.
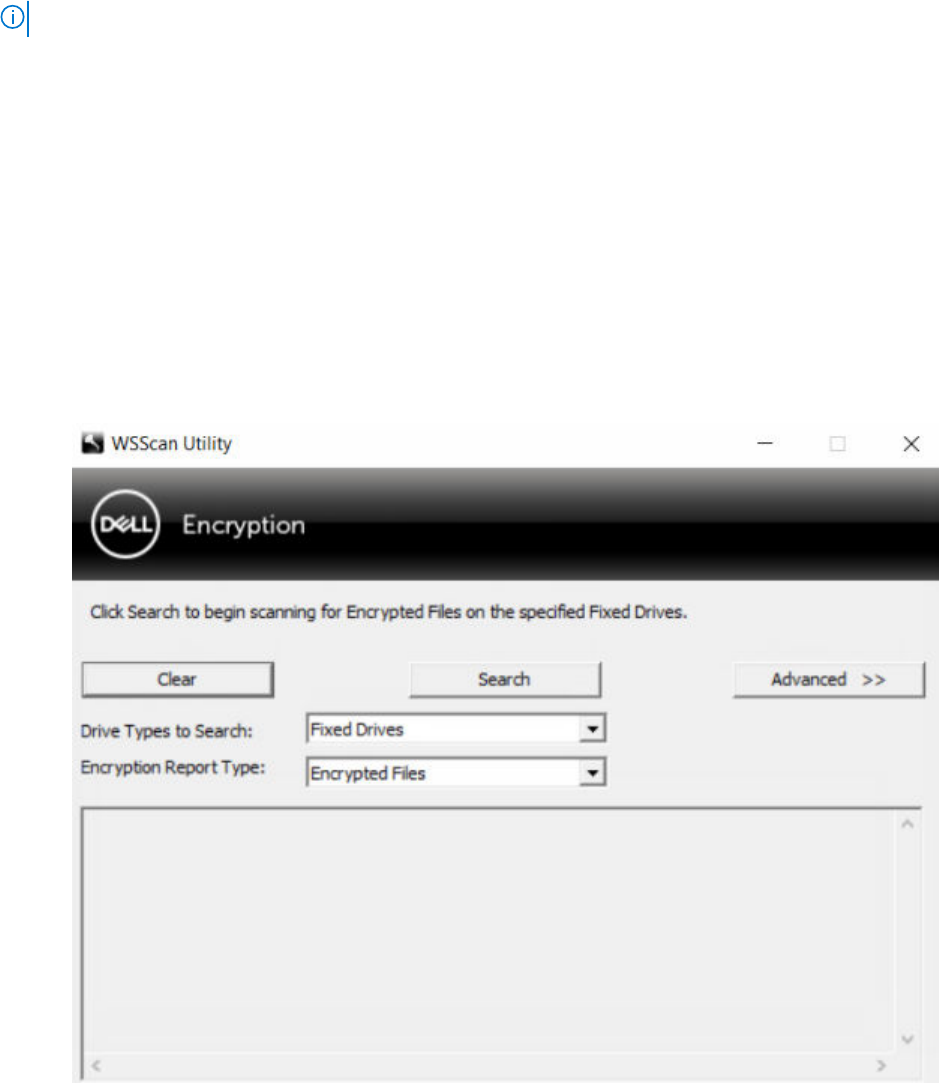
Run WSScan
1. From the Dell installation media, copy WSScan.exe to the Windows computer to scan.
2. Launch a command line at the location above and enter wsscan.exe at the command prompt. WSScan launches.
3. Click Advanced.
4. Select the type of drive to scan: All Drives, Fixed Drives, Removable Drives, or CDROMs/ DVDROMs.
5. Select the Encryption Report Type: Encrypted FIles, Unencrypted FIles, All FIles, or Unencrypted FIles in Violation:
● Encrypted FIles - To ensure that all data is decrypted when uninstalling Encryption. Follow your existing process for
decrypting data, such as issuing a decryption policy update. After decrypting data, but before performing a restart in
preparation for uninstall, run WSScan to ensure that all data is decrypted.
● Unencrypted FIles - To identify files that are not encrypted, with an indication of whether the files should be encrypted
(Y/N).
● All FIles - To list all encrypted and unencrypted files, with an indication of whether the files should be encrypted (Y/N).
● Unencrypted FIles in Violation - To identify files that are not encrypted that should be encrypted.
6. Click Search.
OR
1. Click Advanced to toggle the view to Simple to scan a particular folder.
Troubleshooting
67










