Deployment Guide
Table Of Contents
- Dell Encryption Personal Installation Guide v11.1
- Contents
- Overview
- Requirements
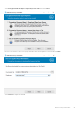
- Download the Software
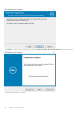
- Installation
- Advanced Authentication and Encryption Personal Setup Wizards
- Configure Console Settings
- Uninstall the Master Installer
- Uninstall Using the Child Installers
- Data Security Uninstaller
- Policies and Template Descriptions
- Policies
- Template Descriptions
- Aggressive Protection for All Fixed Drives and External Drives
- PCI Regulation Targeted
- Data Breach Regulation Targeted
- HIPAA Regulation Targeted
- Basic Protection for All Fixed Drives and External Drives (Default)
- Basic Protection for All Fixed Drives
- Basic Protection for System Drive Only
- Basic Protection for External Drives
- Encryption Disabled
- Extract Child Installers
- Troubleshooting
- Glossary
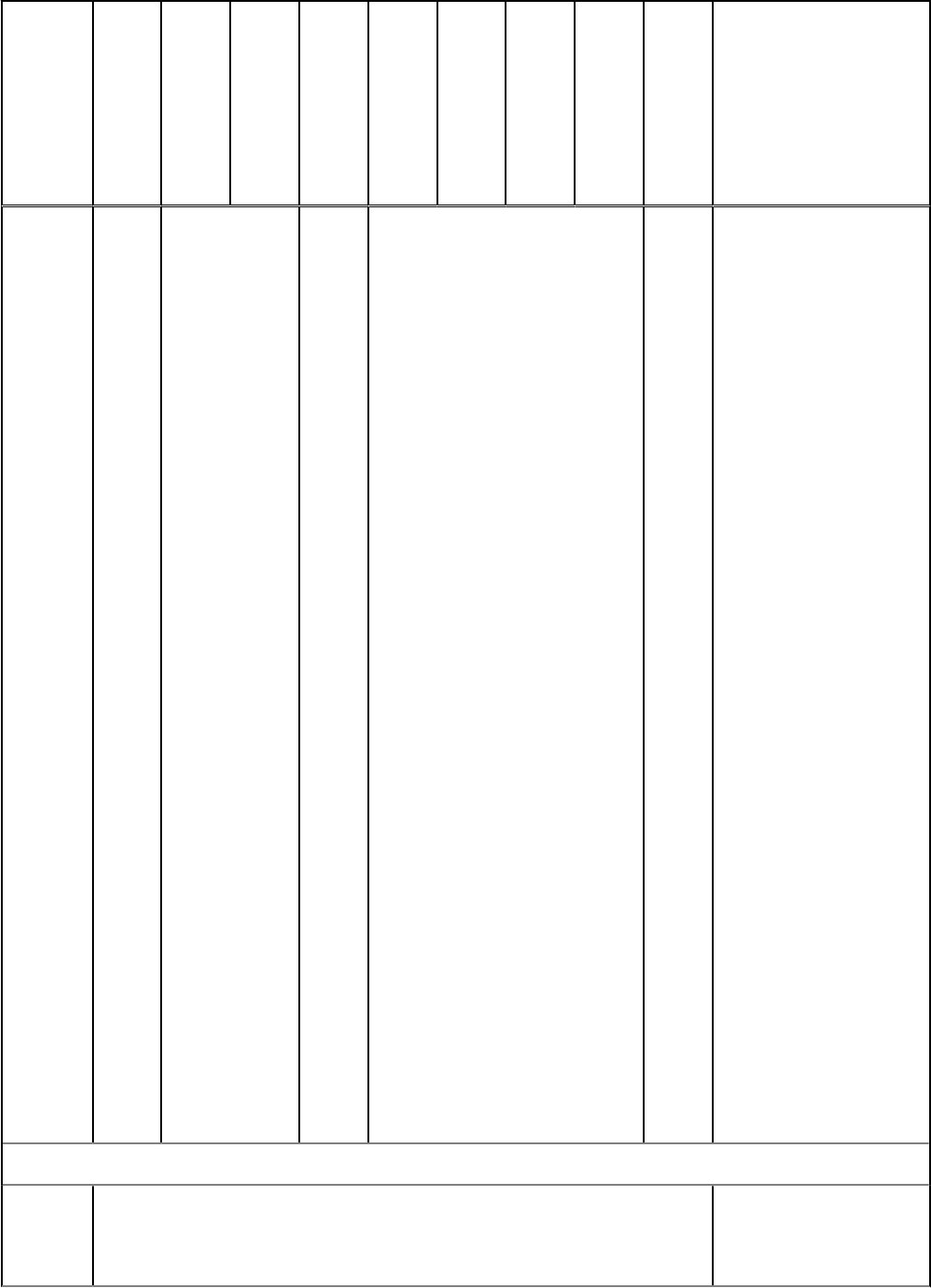
Policy Aggre
ssive
Protec
tion
for All
Fixed
Drives
and
Extern
al
Drives
PCI
Regula
tion
Data
Breac
h
Regula
tion
HIPAA
Regula
tion
Basic
Protec
tion
for All
Fixed
Drives
and
Ext
Drives
(Defau
lt)
Basic
Protec
tion
for All
Fixed
Drives
Basic
Protec
tion
for
Syste
m
Drive
Only
Basic
Protec
tion
for
Extern
al
Drives
Encry
ption
Disabl
ed
Description
• Encrypt Temporary
Files (\Documents and
Settings\username\Local
Settings\Temp only)
• Encrypt Temporary
Internet Files
• Encrypt User Profile
Documents
Select:
• Common for User
Encrypted Files/Folders
to be accessible by
all managed users on
the endpoint where
they were created (the
same level of access
as Common Encrypted
Folders), and encrypted
with the Common
encryption algorithm.
• User for these files to be
accessible only to the user
who created them, only on
the endpoint where they
were created (the same
level of access as User
Encrypted Folders), and
encrypted with the User
encryption algorithm.
If you elect to
incorporate an encryption
policy to encrypt entire
disk partitions, it is
recommended to use the
default SDE encryption
policy, rather than
Common or User. This
ensures that any operating
system files that are
encrypted are accessible
during states when the
managed user is not logged
in.
Hardware Crypto Accelerator (supported only with v8.3 through v8.9.1 Encryption clients)
Hardware
Crypto
Accelerat
or (HCA)
False This policy is the
“master policy” for all
other Hardware Crypto
Accelerator (HCA) policies.
50 Policies and Template Descriptions