Deployment Guide
Table Of Contents
- Dell Encryption Personal Installation Guide v11.1
- Contents
- Overview
- Requirements
- Download the Software
- Installation
- Advanced Authentication and Encryption Personal Setup Wizards
- Configure Console Settings
- Uninstall the Master Installer
- Uninstall Using the Child Installers
- Data Security Uninstaller
- Policies and Template Descriptions
- Policies
- Template Descriptions
- Aggressive Protection for All Fixed Drives and External Drives
- PCI Regulation Targeted
- Data Breach Regulation Targeted
- HIPAA Regulation Targeted
- Basic Protection for All Fixed Drives and External Drives (Default)
- Basic Protection for All Fixed Drives
- Basic Protection for System Drive Only
- Basic Protection for External Drives
- Encryption Disabled
- Extract Child Installers
- Troubleshooting
- Glossary
Uninstall Using the Child Installers
● Dell recommends using the Data Security Uninstaller to remove Encryption Personal.
● The user performing decryption and uninstallation must be a local or domain administrator. If uninstalling by command line,
domain administrator credentials are required.
● If you installed Encryption Personal with the master installer, the child executable files must first be extracted from the
master installer before uninstallation, as shown in Extract the Child Installers from the Master Installer.
● Ensure that the same version of clients is used for uninstallation as installation.
● Plan to decrypt overnight, if possible.
● Turn off sleep mode to prevent an unattended computer from going to sleep. Decryption cannot occur on a sleeping
computer.
● Shut down all processes and applications to minimize failures because of locked files.
Uninstall Encryption
● Before beginning the uninstall process, see (Optional) Create an Encryption Removal Agent Log File. This log file is
useful for troubleshooting an uninstall/decryption operation. If you do not intend to decrypt files during the uninstall process,
you do not need to create an Encryption Removal Agent log file.
NOTE:
Before uninstalling, ensure all policy templates are set to Disabled and insert any encrypted external media for
graceful decryption.
This video details changing policy templates in the Local Management Console.
● Run WSScan to ensure that all data is decrypted after uninstallation is complete, but before restarting the computer. See
Use WSScan for instructions.
● Periodically Check Encryption Removal Agent Status. Data decryption is still in process if the Encryption Removal Agent
service still exists in the services panel.
●
Choose an Uninstallation Method
There are two methods to uninstall the Encryption client, select one of the following:
● Uninstall Interactively
● Uninstall from the Command-Line
Uninstall Interactively
1. Go to Uninstall a Program in the Windows Control Panel (in the search box on the taskbar, type Control Panel, and then
select Control Panel from the results).
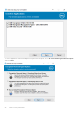
2. Highlight Dell Encryption XX-bit and left-click Change to launch the Encryption Personal Setup Wizard.
3. Read the Welcome screen and click Next.
4. At the Encryption Removal Agent Installation screen, select either:
NOTE:
The second option is enabled by default. If you wish to decrypt files, be sure you change the selection to
option one.
● Encryption Removal Agent - Import Keys from a File
For SDE, User, or Common encryption, this option decrypts files and uninstalls the Encryption client.
This is the
recommended selection
.
8
34 Uninstall Using the Child Installers