Deployment Guide
Table Of Contents
- Dell Encryption Personal Installation Guide v11.1
- Contents
- Overview
- Requirements
- Download the Software
- Installation
- Advanced Authentication and Encryption Personal Setup Wizards
- Configure Console Settings
- Uninstall the Master Installer
- Uninstall Using the Child Installers
- Data Security Uninstaller
- Policies and Template Descriptions
- Policies
- Template Descriptions
- Aggressive Protection for All Fixed Drives and External Drives
- PCI Regulation Targeted
- Data Breach Regulation Targeted
- HIPAA Regulation Targeted
- Basic Protection for All Fixed Drives and External Drives (Default)
- Basic Protection for All Fixed Drives
- Basic Protection for System Drive Only
- Basic Protection for External Drives
- Encryption Disabled
- Extract Child Installers
- Troubleshooting
- Glossary
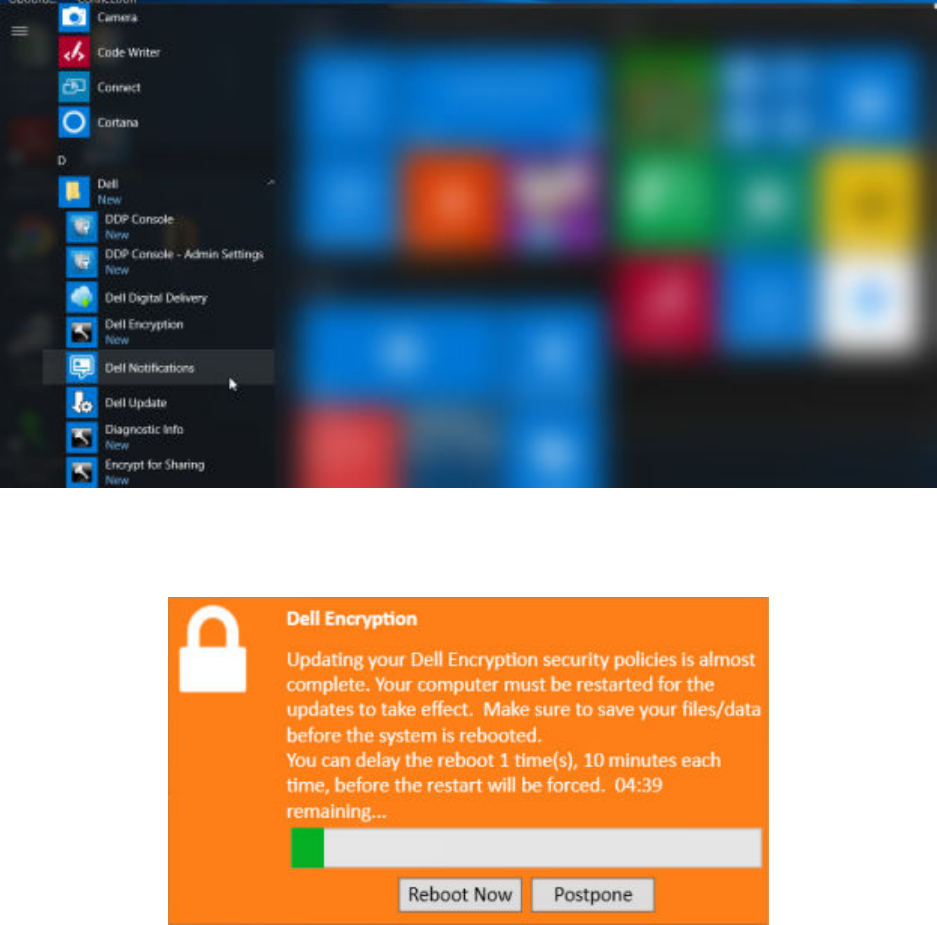
Encryption takes place in the background. The Local Management Console can be opened or closed. Either way, encryption
of files progresses. You can continue to use your computer as usual while it is encrypting.
15. When the scan is complete, the computer reboots once more.
Once all encryption sweeps and reboots are complete, you can verify compliance status by launching the Local Management
Console. The drive is labeled as "In Compliance".
Advanced Authentication and Encryption Personal Setup Wizards
25