Deployment Guide
Table Of Contents
- Dell Encryption Personal Installation Guide v11.1
- Contents
- Overview
- Requirements
- Download the Software
- Installation
- Advanced Authentication and Encryption Personal Setup Wizards
- Configure Console Settings
- Uninstall the Master Installer
- Uninstall Using the Child Installers
- Data Security Uninstaller
- Policies and Template Descriptions
- Policies
- Template Descriptions
- Aggressive Protection for All Fixed Drives and External Drives
- PCI Regulation Targeted
- Data Breach Regulation Targeted
- HIPAA Regulation Targeted
- Basic Protection for All Fixed Drives and External Drives (Default)
- Basic Protection for All Fixed Drives
- Basic Protection for System Drive Only
- Basic Protection for External Drives
- Encryption Disabled
- Extract Child Installers
- Troubleshooting
- Glossary

Installation
You can install Encryption Personal using the master installer (recommended), or by extracting the child installers from the
master installer. Either way, Encryption Personal can be installed by user interface, command line or scripts, and using any push
technology available to your organization.
Users should see the following help files for application assistance:
NOTE: If Policy-Based Encryption is installed before the Encryption Management Agent, computer crash may occur. This
issue is caused by failure to load the encryption Sleep driver that manages the PBA environment. As a workaround, use the
master installer or ensure that Policy-Based Encryption is installed after the Encryption Management Agent.
● See the Dell Encrypt Help to learn how to use the features of Encryption. Access the help from <Install
dir>\Program Files\Dell\Dell Data Protection\Encryption\Help.
● See the Encryption External Media Help to learn how the features of Encryption External Media. Access the help from
<Install dir>\Program Files\Dell\Dell Data Protection\Encryption.
● See the Encryption Personal Help to learn how to use the features of Advanced Authentication. Access the help from
<Install dir>\Program Files\Dell\Dell Data Protection\Security Tools\Help.
Import Entitlement
Installation of Encryption Personal requires a registry key on the target computer. This registry key is added through Command
Line interface during installation or through the GUI prior to installation.
To add the registry key through Command Line interface, see Command-Line Installation .
To add the registry key through the GUI:
1. Open a text editor.
2. Add the following text.
[HKEY_LOCAL_MACHINE\Software\Dell\Dell Data Protection\Entitlement]
"SaEntitlement"="1:PE:{XXXXX-XXX-XXXX-XXX-XXXX-
XXXXXXXXXXXX}:xXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX="
3. Save the text file with the .reg extension.
4. Double-click the saved registry file to import the Encryption Personal entitlement.
Choose an Installation Method
There are two methods to install the client, select one of the following:
● Install Interactively - RECOMMENDED
● Command-Line Installation
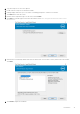
Interactive Installation
To install Encryption Personal, the installer must find the appropriate entitlement on the computer. If the appropriate
entitlement is not found, Encryption Personal cannot be installed.
● The Master Installer installs multiple clients. In the case of Encryption Personal, it installs Encryption and SED management.
● Master installer log files are located at C:\ProgramData\Dell\Dell Data Protection\Installer.
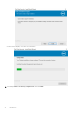
1. Install the entitlement on the target computer if needed. Instructions for adding the entitlement to the computer are
included with the email that discusses license information.
4
14 Installation