User's Manual
Table Of Contents
- Cybersecurity Recommendations
- Regulatory Information
- Foreword
- 1 Product Introduction
- 2 Basic Settings
- 3 Daily Operation
- 3.1 Live
- 3.2 PTZ
- 3.2.1 Bullet Camera
- 3.2.2 Dome Camera
- 3.2.2.1 Configuring Protocol
- 3.2.2.2 Configuring PTZ Functions
- 3.2.2.2.1 Configuring Preset
- 3.2.2.2.2 Configuring Tour
- 3.2.2.2.3 Configuring Scan
- 3.2.2.2.4 Configuring Pattern
- 3.2.2.2.5 Configuring Pan
- 3.2.2.2.6 Configuring PTZ Speed
- 3.2.2.2.7 Configuring Idle Motion
- 3.2.2.2.8 Configuring Power Up
- 3.2.2.2.9 Configuring Time Task
- 3.2.2.2.10 Restarting PTZ Manually
- 3.2.2.2.11 Restoring PTZ to the Default Settings
- 3.2.2.3 Operating PTZ
- 3.2.2.4 Configuring Preset Backup
- 3.3 Playback
- 3.4 Reports
- 3.5 Alarm
- 4 Setting
- 4.1 Configuring Camera
- 4.1.1 Configuring Lens
- 4.1.2 Configuring Video Parameters
- 4.1.3 Configuring Audio Parameters
- 4.2 Configuring Network
- 4.3 Peripheral
- 4.4 Smart Thermal
- 4.5 Event
- 4.6 Temperature Measuring Settings
- 4.7 Storage Management
- 4.8 System Management
- 4.1 Configuring Camera
- 5 System Maintenance
- 6 Additional Accessing Methods
Setting 141
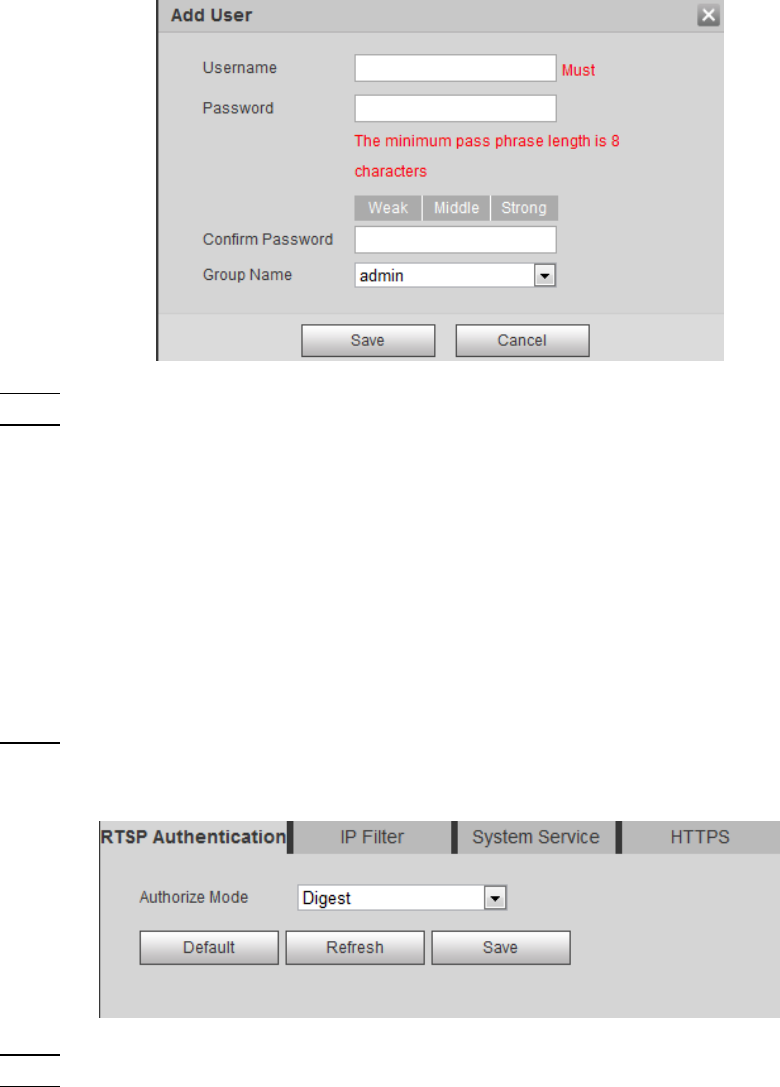
Add user Figure 4-95
Enter username, password and confirm the password. Then, select group name. Step 3
Click Save to finish configuration. Step 4
4.8.4 Safety Management
Set RTSP authentication, IP filter, system service and HTTPS to secure data transmission and
prevent data leakage.
4.8.4.1 Configuring RTSP Authentication
RTSP (Real Time Streaming Protocol) is to secure transmission of streaming media.
Select Setting > System > Security > RTSP Authentication. Step 1
The RTSP Authentication interface is displayed. See Figure 4-96.
RTSP authentication Figure 4-96
Select an authentication mode. Step 2
Click Save. Step 3
4.8.4.2 Configuring IP Filter
To secure the network environment and protect your data, you can use IP filter to set who can
and who cannot access your device.
White list: Only users whose IP/MAC are on the white list can access your device.
Black list: Only users whose IP/MAC are on the black list cannot access your device.
Only when IP addresses of both your device and your PC are located in the same LAN,
can MAC verification takes effect.










