User's Manual
Table Of Contents
- Foreword
- Important Safeguards and Warnings
- 1 Overview
- 2 Configuration Flow
- 3 Device Initialization
- 4 Basic Configuration
- 4.1 Login
- 4.2 Live
- 4.3 PTZ Operation
- 4.4 Playback
- 4.5 Camera
- 4.5.1 Conditions
- 4.5.2 Setting Video Parameters
- 4.5.2.1 Video
- 4.5.2.2 Snapshot
- 4.5.2.3 Overlay
- 4.5.2.3.1 Configuring Privacy Masking
- 4.5.2.3.2 Configuring Channel Title
- 4.5.2.3.3 Configuring Time Title
- 4.5.2.3.4 Configure Text Overlay
- 4.5.2.3.5 Configure Font Attribute
- 4.5.2.3.6 Configure Picture Overlay
- 4.5.2.3.7 Configure Custom Overlay
- 4.5.2.3.8 Configuring OSD Info
- 4.5.2.3.9 Configuring Counting
- 4.5.2.3.10 Configuring Structured Statistics
- 4.5.2.3.11 Configuring Ranging
- 4.5.2.3.12 Configuring ANPR
- 4.5.2.3.13 Configuring Face Statistics
- 4.5.2.4 ROI
- 4.5.2.5 Path
- 4.5.3 Audio
- 4.6 Network
- 4.7 Storage
- 4.8 System
- 5 Event
- 5.1 Setting Alarm Linkage
- 5.2 Setting Smart Track
- 5.3 Setting Panoramic Calibration
- 5.4 Setting Video Detection
- 5.5 Setting Smart Motion Detection
- 5.6 Setting Audio Detection
- 5.7 Setting Smart Plan
- 5.8 Setting IVS
- 5.9 Setting Crowd Map
- 5.10 Setting Face Recognition
- 5.11 Setting Face Detection
- 5.12 Setting People Counting
- 5.13 Setting Heat Map
- 5.14 Setting Stereo Analysis
- 5.15 Setting ANPR
- 5.16 Setting Video Structuralization
- 5.17 Setting Relay-in
- 5.18 Setting Abnormality
- 6 Maintenance
- Appendix 1 Cybersecurity Recommendations
User’s Manual
103
The newly added user displays in the user name list.
After adding user, click to modify password, group, memo or authorities;
click to delete the added user. Admin user cannot be deleted.
Click in the admin row to modify its username and email address.
4.8.5 Safety
You can configure system service, HTTPS, and Firewall.
4.8.5.1 System Service
Configure the IP hosts (devices with IP address) that are allowed to visit the device. Only the
hosts in the trusted sites list can log in to the web interface. This is to enhance network and
data security.
Select Setting > System > Safety > System Service. Step 1
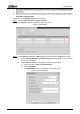
The System Service interface is displayed. See Figure 4-99.
System service Figure 4-99
Enable the system service according to the actual needs. For details, see Table 4-39. Step 2
Table 4-39 Description of system service parameters
Function
Description
SSH
You can enable SSH authentication to perform safety management.
Multicast/Broadcast
Search
Enable this function, and then when multiple users are previewing the
device video image simultaneously through network, they can find