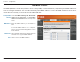
Section 3 - Configuration Network Filters Use MAC (Media Access Control) Filters to allow or deny LAN (Local Area Network) computers by their MAC addresses from accessing the Network. You can either manually add a MAC address or select the MAC address from the list of clients that are currently connected to the Broadband Router. Configure MAC Select Turn MAC Filtering Off, Allow MAC Filtering: addresses listed below, or Deny MAC addresses listed below from the drop-down menu.
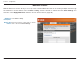
Section 3 - Configuration Access Control The Access Control section allows you to control access in and out of your network. Use this feature as Parental Controls to only grant access to approved sites, limit web access based on time or dates, and/or block access from applications like P2P utilities or games. Add Policy: Click the Add Policy button to start the Access Control Wizard. Access Control Wizard Click Next to continue with the wizard.
Section 3 - Configuration Access Control Wizard (continued) Enter a name for the policy and then click Next to continue. Select a schedule (I.E. Always) from the drop-down menu and then click Next to continue. Enter the following information and then click Next to continue. • Address Type - Select IP address, MAC address, or Other Machines. • IP Address - Enter the IP address of the computer you want to apply the rule to.
Section 3 - Configuration Access Control Wizard (continued) Select the filtering method and then click Next to continue. Enter the rule: Enable - Check to enable the rule. Name - Enter a name for your rule. Dest IP Start - Enter the starting IP address. Dest IP End - Enter the ending IP address. Protocol - Select the protocol. Dest Port Start - Enter the starting port number. Dest Port End - Enter the ending port number. To enable web logging, click Enable. Click Save to save the access control rule.
Section 3 - Configuration Website Filters Website Filters are used to allow you to set up a list of allowed Web sites that can be used by multiple users through the network. To use this feature select to Allow or Deny, enter the domain or website and click Save Settings. You must also select Apply Web Filter under the Access Control section (page 40). Add Website Select Allow or Deny. Filtering Rule: Website URL/ Enter the keywords or URLs that you want to Domain: allow or block. Click Save Settings.
Section 3 - Configuration Inbound Filters The Inbound Filter option is an advanced method of controlling data received from the Internet. With this feature you can configure inbound data filtering rules that control data based on an IP address range. Inbound Filters can be used with Virtual Server, Port Forwarding, or Remote Administration features. Name: Enter a name for the inbound filter rule. Action: Select Allow or Deny. Enable: Check to enable rule. Remote IP Start: Enter the starting IP address.
Section 3 - Configuration Firewall Settings A firewall protects your network from the outside world. The DIR-855 offers a firewall type functionality. The SPI feature helps prevent cyber attacks. Sometimes you may want a computer exposed to the outside world for certain types of applications. If you choose to expose a computer, you can enable DMZ. DMZ is short for Demilitarized Zone. This option will expose the chosen computer completely to the outside world.
Section 3 - Configuration Application Level Gateway (ALG) Configuration Here you can enable or disable ALG’s. Some protocols and applications require special handling of the IP payload to make them work with network address translation (NAT). Each ALG provides special handling for a specific protocol or application. A number of ALGs for common applications are enabled by default. PPTP: Allows multiple machines on the LAN to connect to their corporate network using PPTP protocol.
Section 3 - Configuration Advanced Wireless Settings 802.11n/g (2.4GHz) Transmit Power: Set the transmit power of the antennas. Beacon Period: Beacons are packets sent by an Access Point to synchronize a wireless network. Specify a value. 100 is the default setting and is recommended. RTS Threshold: This value should remain at its default setting of 2432. If inconsistent data flow is a problem, only a minor modification should be made.
Section 3 - Configuration Advanced Wireless Settings 802.11n/a (5GHz) Transmit Power: Set the transmit power of the antennas. Beacon Period: Beacons are packets sent by an Access Point to synchronize a wireless network. Specify a value. 100 is the default setting and is recommended. RTS Threshold: This value should remain at its default setting of 2432. If inconsistent data flow is a problem, only a minor modification should be made.
Section 3 - Configuration WISH Settings WISH is short for Wireless Intelligent Stream Handling, a technology developed to enhance your experience of using a wireless network by prioritizing the traffic of different applications. Enable WISH: Enable this option if you want to allow WISH to prioritize your traffic. HTTP: Allows the router to recognize HTTP transfers for many common audio and video streams and prioritize them above other traffic. Such streams are frequently used by digital media players.
Section 3 - Configuration Name: Create a name for the rule that is meaningful to you. Priority: The priority of the message flow is entered here. The four priorities are defined as: BK: Background (least urgent) BE: Best Effort. VI: Video VO: Voice (most urgent) Protocol: The protocol used by the messages. Host IP Range: The rule applies to a flow of messages for which one computer’s IP address falls within the range set here.
Section 3 - Configuration Advanced Network Settings Enable UPnP: To use the Universal Plug and Play (UPnP™) feature click on Enabled. UPNP provides compatibility with networking equipment, software and peripherals. WAN Ping: Unchecking the box will not allow the DIR-855 to respond to pings. Blocking the Ping may provide some extra security from hackers. Check the box to allow the Internet port to be “pinged”.
Section 3 - Configuration Administrator Settings This page will allow you to change the Administrator and User passwords. You can also enable Remote Management. There are two accounts that can access the management interface through the web browser. The accounts are admin and user. Admin has read/write access while user has read-only access. User can only view the settings but cannot make any changes. Only the admin account has the ability to change both admin and user account passwords.
Section 3 - Configuration Time Settings The Time Configuration option allows you to configure, update, and maintain the correct time on the internal system clock. From this section you can set the time zone that you are in and set the Time Server. Daylight Saving can also be configured to automatically adjust the time when needed. Time Zone: Select the Time Zone from the drop-down menu.
Section 3 - Configuration SysLog The Broadband Router keeps a running log of events and activities occurring on the Router. You may send these logs to a SysLog server on your network. Enable Logging to Check this box to send the router logs to a SysLog Server: SysLog Server. SysLog Server IP The address of the SysLog server that will be Address: used to send the logs. You may also select your computer from the drop-down menu (only if receiving an IP address from the router via DHCP).
Section 3 - Configuration Email Settings The Email feature can be used to send the system log files, router alert messages, and firmware update notification to your email address. Enable Email When this option is enabled, router activity logs Notification: are e-mailed to a designated email address. From Email This email address will appear as the sender Address: when you receive a log file or firmware upgrade notification via email. To Email Address: Enter the email address where you want the email sent.
Section 3 - Configuration System Settings This section allows you to manage the router’s configuration settings, reboot the router, and restore the router to the factory default settings. Restoring the unit to the factory default settings will erase all settings, including any rules that you’ve created. Save Settings to Use this option to save the current router Local Hard Drive: configuration settings to a file on the hard disk of the computer you are using. First, click the Save button.
Section 3 - Configuration Update Firmware You can upgrade the firmware of the Router here. Make sure the firmware you want to use is on the local hard drive of the computer. Click on Browse to locate the firmware file to be used for the update. Please check the D-Link support site for firmware updates at http://support.dlink.com. You can download firmware upgrades to your hard drive from the D-Link support site.
Section 3 - Configuration DDNS The DDNS feature allows you to host a server (Web, FTP, Game Server, etc…) using a domain name that you have purchased (www.whateveryournameis.com) with your dynamically assigned IP address. Most broadband Internet Service Providers assign dynamic (changing) IP addresses. Using a DDNS service provider, your friends can enter in your domain name to connect to your server no matter what your IP address is.
Section 3 - Configuration System Check Ping Test: The Ping Test is used to send Ping packets to test if a computer is on the Internet. Enter the IP Address that you wish to Ping, and click Ping. Ping Results: The results of your ping attempts will be displayed here.
Section 3 - Configuration Schedules Schedules can be created for use with enforcing rules. For example, if you want to restrict web access to Mon-Fri from 3pm to 8pm, you could create a schedule selecting Mon, Tue, Wed, Thu, and Fri and enter a Start Time of 3pm and End Time of 8pm. Name: Enter a name for your new schedule. Days: Select a day, a range of days, or All Week to include every day. Time: Check All Day - 24hrs or enter a start and end time for your schedule.
Section 3 - Configuration Device Information This page displays the current information for the DIR-855. It will display the LAN, WAN (Internet), and Wireless information. If your Internet connection is set up for a Dynamic IP address then a Release button and a Renew button will be displayed. Use Release to disconnect from your ISP and use Renew to connect to your ISP. If your Internet connection is set up for PPPoE, a Connect button and a Disconnect button will be displayed.
Section 3 - Configuration Log The router automatically logs (records) events of possible interest in it’s internal memory. If there isn’t enough internal memory for all events, logs of older events are deleted but logs of the latest events are retained. The Logs option allows you to view the router logs. You can define what types of events you want to view and the level of the events to view.
Section 3 - Configuration Stats The screen below displays the Traffic Statistics. Here you can view the amount of packets that pass through the DIR-855 on both the Internet, LAN ports and both the 802.11n/g and 802.11a wireless bands. The traffic counter will reset if the device is rebooted.
Section 3 - Configuration Internet Sessions The Internet Sessions page displays full details of active Internet sessions through your router. An Internet session is a conversation between a program or application on a LAN-side computer and a program or application on a WAN-side computer.
Section 3 - Configuration Wireless The wireless client table displays a list of current connected wireless clients. This table also displays the connection time and MAC address of the connected wireless clients. WISH The WISH details page displays full details of wireless clients that are connected when WISH is enabled.
Section 3 - Configuration Support D-Link DIR-855 User Manual 66
Section 4 - Security Wireless Security This section will show you the different levels of security you can use to protect your data from intruders. The DIR-855 offers the following types of security: • WPA2 (Wi-Fi Protected Access 2) • WPA (Wi-Fi Protected Access) • WPA2-PSK (Pre-Shared Key) • WPA-PSK (Pre-Shared Key) What is WPA? WPA, or Wi-Fi Protected Access, is a Wi-Fi standard that was designed to improve the security features of WEP (Wired Equivalent Privacy).
Section 4 - Security Wireless Security Setup Wizard To run the security wizard, click on Setup at the top and then click Launch Wireless Security Setup Wizard. Check the Manually set 5GHz band Network Name... box to manually set your desired wireless network name for the 5GHz band. Type your desired wireless network name (SSID). Automatically: Select this option to automatically generate the router’s network key and click Next.
Section 4 - Security If you selected Automatically, the summary window will display your settings. Write down the security key and enter this on your wireless clients. Click Save to save your settings.
Section 4 - Security Add Wireless Device with WPS Wizard From the Basic > Wizard screen, click Add Wireless Device with WPS. Select Auto to add a wireless client using WPS (Wi-Fi Protected Setup). Once you select Auto and click Connect, you will have a 120 second time limit to apply the settings to your wireless client(s) and successfully establish a connection. If you select Manual, a settings summary screen will appear. Write down the security key and enter this on your wireless clients.
Section 4 - Security Configure WPA-Personal (PSK) It is recommended to enable encryption on your wireless router before your wireless network adapters. Please establish wireless connectivity before enabling encryption. Your wireless signal may degrade when enabling encryption due to the added overhead. 1. Log into the web-based configuration by opening a web browser and entering the IP address of the router (192.168.0.1). Click on Setup and then click Wireless Settings on the left side. 2.
Section 4 - Security Configure WPA-Enterprise (RADIUS) It is recommended to enable encryption on your wireless router before your wireless network adapters. Please establish wireless connectivity before enabling encryption. Your wireless signal may degrade when enabling encryption due to the added overhead. 1. Log into the web-based configuration by opening a web browser and entering the IP address of the router (192.168.0.1). Click on Setup and then click Wireless Settings on the left side. 2.
Section 4 - Security 8. Next to RADIUS Server Port, enter the port you are using with your RADIUS server. 1812 is the default port. 9. Next to RADIUS Server Shared Secret, enter the security key. 10. If the MAC Address Authentication box is selected then the user will need to connect from the same computer whenever logging into the wireless network. 11. Click Advanced to enter settings for a secondary RADIUS Server. 12. Click Apply Settings to save your settings.
Section 4 - Security Connect to a Wireless Network Using Windows® Vista™ Windows® Vista™ users may use the built-in wireless utility. If you are using another company’s utility or Windows® 2000, please refer to the user manual of your wireless adapter for help with connecting to a wireless network. Most utilities will have a “site survey” option similar to the Windows® Vista™ utility as seen below.
Section 5 - Connecting to a Wireless Network Configure Wireless Security It is recommended to enable wireless security (WPA/WPA2) on your wireless router or access point before configuring your wireless adapter. If you are joining an existing network, you will need to know the security key or passphrase being used. 1. Open the Windows® Vista™ Wireless Utility by right-clicking on the wireless computer icon in your system tray (lower right corner of screen). Select Connect to a network. 2.
Section 5 - Connecting to a Wireless Network 3. Enter the same security key or passphrase that is on your router and click Connect. It may take 20-30 seconds to connect to the wireless network. If the connection fails, please verify that the security settings are correct. The key or passphrase must be exactly the same as on the wireless router.
Section 5 - Connecting to a Wireless Network Connect Using WCN 2.0 in Windows Vista™ The router supports Wi-Fi protection, referred to as WCN 2.0 in Windows Vista™. The following instructions for setting this up depends on whether you are using Windows Vista™ to configure the router or third party software. When you first set up the router, Wi-Fi protection is disabled and unconfigured. To enjoy the benefits of Wi-Fi protection, the router must be both enabled and configured.
Section 5 - Connecting to a Wireless Network Connect to a Wireless Network Using Windows® XP Windows® XP users may use the built-in wireless utility (Zero Configuration Utility). The following instructions are for Service Pack 2 users. If you are using another company’s utility or Windows® 2000, please refer to the user manual of your wireless adapter for help with connecting to a wireless network. Most utilities will have a “site survey” option similar to the Windows® XP utility as seen below.
Section 5 - Connecting to a Wireless Network Configure WPA-PSK It is recommended to enable WPA on your wireless router or access point before configuring your wireless adapter. If you are joining an existing network, you will need to know the WPA key being used. 1. Open the Windows® XP Wireless Utility by right-clicking on the wireless computer icon in your system tray (lower-right corner of screen). Select View Available Wireless Networks. 2.
Section 5 - Connecting to a Wireless Network 3. The Wireless Network Connection box will appear. Enter the WPA-PSK passphrase and click Connect. It may take 20-30 seconds to connect to the wireless network. If the connection fails, please verify that the WPA-PSK settings are correct. The WPA-PSK passphrase must be exactly the same as on the wireless router.