Data Sheet
RLGE2FE16R
Substation-Rated, Enhanced Security SCADA-Aware Ethernet Layer 2 Managed
Switch/Layer 3 Router With Optional 2G/3G & 4G LTE Cellular Radio Link,
Enhanced Network Security, Terminal Server, PoE+, and 100FX SFP Ports
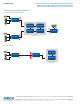
Event logger
The event logger feature allows the operator to receive events and logs from any number of remote OT devices. It supports
multiple formats (Syslog, SNMP, & HTTP), and is also capable of polling event tables from IP, access control, and serial data
devices. The events are received and sent outbound in Syslog format, with additional fields appended, completing a unified
Event Log Aggregator (e.g. location, source sub-system, and severity). Following this aggregation, the Event Logger stores
normalized events locally, and forwards formatted events upstream to a central SIEM tool, providing encrypted, reliable, and
guaranteed logging in accordance with NERC-CIP-5 standards.
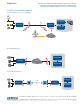
X.509 Certificate Exchange for VPN Connections
VPN tunnels for secure inter-site connectivity with IPsec VPN, GRE Tunnels, and DMVPN technologies are fully supported. In
addition to IPsec encryption, X.509 key management certificates are provided. This certificate support allows for a secure signed
key exchange between a Certificate Authority, and two secure nodes. Having a third-party authority as a signing participant
offers end-to-end security that may be managed and reissued from a trusted central source within the user’s network.
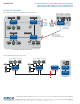
Cyber-Physical Integration
Integrated within the enhanced-security RLGE2FE16R, is a physical identity server system, allowing the use of external
authentication hardware, such as magnetic card readers, biometric identification sensors, facial recognition cameras, etc., to
create a two-factor authentication to the APA feature. This provides an additional level of validation of the user and his/her
credentials, prior to granting the user network access. Once the authentication is validated and approved, a set of defined
policies allow the authenticated technician to perform their task.
The cyber-physical integration also allows the Event Logger feature to poll and deliver events from physical access control
assets and devices. These assets include but are not limited to access control panels and access control head-end systems
and databases.
Enhanced SCADA-Aware Firewall
A whitelist-based firewall is provided for every Ethernet and serial data port, so full firewall protection is available at all remote
sites within the network. Every SCADA protocol packet (IEC 61850, DNP3 RTU/TCP, ModBus RTU/TCP, and IEC 101/104) is
scanned and validated by the firewall engine for its source and destination, as well as its protocol and packet content.
The structure of the distributed firewall allows the creation of a unique firewall at each access point to the network. This is critical
for securing against insider cyber-attacks, compromised field devices, man-in-the-middle attacks, and a myriad of alternate
attack vectors, by providing a secure baseline.
Two firewall states are included: Monitoring, and enforcing. The monitoring state provides an alarm at the control center for any
network violation, without blocking the network traffic. The enforcing state is extremely effective for blocking suspicious traffic,
while also triggering a violation alarm at the control center.
DPI (Deep Packet Inspection) SCADA Protocols Firewall
ComNet’s distributed DPI firewall ensures that the operator will have full control over the network, even when faced with a
sophisticated attempt at breaching the network. Monitoring SCADA commands, this highly robust whitelist-based firewall
analyses SCADA network traffic, and is provided for every Ethernet and serial data port, so full firewall protection is available
at all remote sites within the network, as well as all IEDs, RTUs, PLCs, or any other device connected to the network. Every
SCADA protocol packet (IEC 61850, DNP3 RTU/TCP, ModBus RTU/TCP, and IEC 101/104) is scanned and validated by the
firewall engine for its source and destination, as well as its protocol and its specific packet
Any detected abnormal traffic behavioral patterns are blocked, any affected subnets are isolated, and alerts are
automatically generated.
Ease of Installation and Network Integration
High levels of cyber-security experience are not required to successfully deploy the RLGE2FE16R. It is fully supported by
ComNet’s Reliance Product Configuration Utility and CLI, allowing the secure switch/router to be easily configured, and to
diagnose network and security functions.
Configuration of the secure firewall is also simple. Once connected to the user’s network, the RLGE2FE16R immediately
begins to collect and analyse information across the network, including from other connected devices, traffic behavior, etc.
PRODUCT DESCRIPTION (Cont’d)
LIFETIME WARRANTY WWW.COMNET.NET TECH SUPPORT: 1.888.678.9427