Troubleshooting guide
1-8
Cisco Wide Area Application Services Configuration Guide
OL-26579-01
Chapter 1 Configuring Administrative Login Authentication, Authorization, and Accounting
Configuring Administrative Login Authentication and Authorization
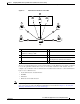
Figure 1-2 SSH Configuration Window
Step 3 Check the Enable check box to enable the SSH feature. SSH enables login access to the chosen WAAS
device (or the device group) through a secure and encrypted channel.
Step 4 Check the Allow non-admin users check box to allow non-administrative users to gain SSH access to
the chosen device (or device group). By default, this option is disabled.
Note Nonadministrative users are non-superuser administrators. All non-superuser administrators
only have restricted access to a WAAS device because their login accounts have a privilege level
of 0. Superuser administrators have full access to a WAAS device because their login accounts
have the highest level of privileges, a privilege level of 15.
Step 5 In the Length of key field, specify the number of bits needed to create an SSH key. The default is 1024.
When you enable SSH, be sure to generate both a private and a public host key, which client programs
use to verify the server’s identity. When you use an SSH client and log in to a WAAS device, the public
key for the SSH daemon running on the device is recorded in the client machine known_hosts file in your
home directory. If the WAAS administrator subsequently regenerates the host key by specifying the
number of bits in the Length of key field, you must delete the old public key entry associated with the
WAAS device in the known_hosts file before running the SSH client program to log in to the WAAS
device. When you use the SSH client program after deleting the old entry, the known_hosts file is
updated with the new SSH public key for the WAAS device.
Step 6 In the Login grace time field, specify the number of seconds for which an SSH session will be active
during the negotiation (authentication) phase between client and server before it times out. The default
is 300 seconds.
Step 7 In the Maximum number of password guesses field, specify the maximum number of incorrect password
guesses allowed per connection. The default is 3.
Although the value in the Maximum number of password guesses field specifies the number of allowed
password guesses from the SSH server side, the actual number of password guesses for an SSH login
session is determined by the combined number of allowed password guesses of the SSH server and the
SSH client. Some SSH clients limit the maximum number of allowed password guesses to three (or to
one in some cases), even though the SSH server allows more than this number of guesses. When you
specify n allowed password guesses, certain SSH clients interpret this number as n + 1. For example,
when configuring the number of guesses to two for a particular device, SSH sessions from some SSH
clients will allow three password guesses.
Step 8 Specify whether the clients should be allowed to connect using the SSH protocol Version 1 or Version 2: