Troubleshooting guide
1-3
Cisco Wide Area Application Services Configuration Guide
OL-26579-01
Chapter 1 Configuring Administrative Login Authentication, Authorization, and Accounting
About Administrative Login Authentication and Authorization
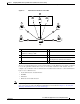
Figure 1-1 Authentication Databases and a WAE
The user account information is stored in an AAA database, and the WAAS devices must be configured
to access the particular authentication server (or servers) that contains the AAA database. You can
configure any combination of these authentication and authorization methods to control administrative
login access to a WAAS device:
• Local authentication and authorization
• RADIUS
• TACACS+
• Windows domain authentication
Note If you configure authentication using an external authentication server, you still must create a role-based
user or user group account in the WAAS Central Manager as described in Chapter 1, “Creating and
Managing Administrator User Accounts and Groups.”
1 FTP/SFTP client 6 Windows domain server
2 WAAS Central Manager GUI or
WAE Device Manager GUI
7 Console or Telnet clients
3 Third-party AAA servers 8 SSH client
4 RADIUS server 9 WAE that contains a local database and the
default primary authentication database
5 TACACS+ server 10 Administrative login requests
159092
1
2
3
4
5
6
7
8
9
10
10
10
10