Product data
Table Of Contents
- Contents
- Introduction
- Networked Storage Overview
- Storage Concepts and Technologies
- Conclusion
- Obtaining Technical Assistance
- Appendix A
Storage Concepts and Technologies
Figure 13: RAID 10
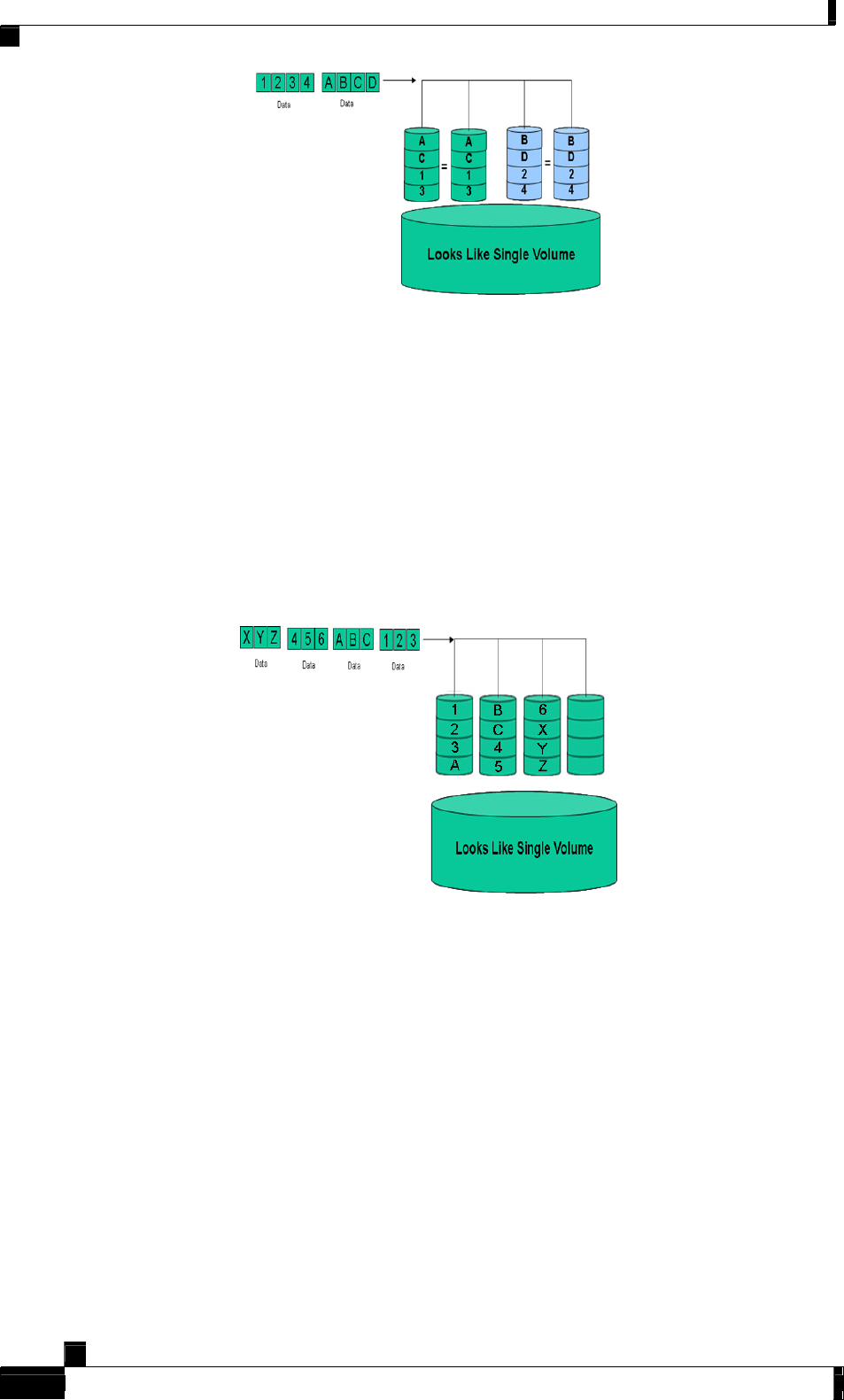
JBOD – (Linear) - (Just a Bunch of Disks)
JBOD is technically not one of the numbered RAID levels. It provides a way to group a set of
physical disks together to appear to the operating system as a single disk (Figure 14). With a
JBOD, you can concatenate disks of varying sizes into one logical unit. For example, one
drive could be 3 GB, one 15 GB, one 5.5 GB to make a logical drive of 23.5 GB. The following
design considerations apply:
• Advantages: Disks of varied sizes can form a single logical unit. Unlike RAID 0, if a
single drive fails in a JBOD, only the data on the affected drive is lost. In a RAID 0, this
usually means the loss of all the data in the array.
• Disadvantages: There are no performance benefits and there is no data protection.
Figure 14: JBOD
Storage Security
Storage networks have traditionally been considered "secure" because deployments have
been limited to a subset of a single data center on an isolated network. This perception is
changing with the reach of storage networks over the Internet. It is becoming more common
to read about information assets (sensitive proprietary data, credit card information, etc.)
being compromised via unauthorized storage access. Unlike other storage vendors, Cisco
and Linksys have a legacy of securing networks for our customers. Linksys is uniquely
qualified to help protect precious information from both externally and internally launched
attacks with the following capabilities that are built into Linksys NSS products.
Access Control
NSS secure access control allows the business to limit or allow access to the NSS and
volumes on an as needed basis. Access to the system in general is controlled by user ID and
password authentication, generally in conjunction with a directory service (as described
White Paper: Network Storage LINKSYS © 2007
14 EDCS-593805 v1.0
A printed copy of this document is considered uncontrolled










