User guide
Task 5: Configuring security Chapter 6: Configuration and alignment
6-38
phn-2513_004v000 (Oct 2012)
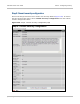
Step 6: Enter the wireless link encryption key
The Step 6: Enter The Wireless Link Encryption Key page is displayed (Figure 128). The
wireless link encryption key is used to encrypt all traffic over the PTP 800 wireless link.
Select the applicable value in the Encryption Algorithm field. If a valid encryption key
exists, then an SHA-1 thumbprint of the key is displayed. If this key is correct, then take no
action. Otherwise, enter the generated key in the Wireless Link Encryption Key and
Confirm Wireless Link Encryption Key fields. Select Next.
Figure 128 Step 6: Enter Wireless Link Encryption Key page