Manual
Table Of Contents
- Preface
- Introduction
- Process Summary
- Prerequisites
- Run the Service Setup Wizard
- VCS System Configuration
- Routing Configuration
- Pre-search Transforms
- Search Rules
- Task 8: Configuring Transforms
- Task 9: Configuring Local Zone Search Rules
- Task 10: Configuring the Traversal Zone
- Neighboring Between VCS Clusters
- Task 11: Configuring Traversal Zone Search Rules
- Task 12: Configuring the DNS Zone
- Task 13: Configuring DNS Zone Search Rules
- Task 14: Configuring External (Unknown) IP Address Routing
- Endpoint Registration
- System Checks
- Maintenance Routine
- Optional Configuration Tasks
- Appendix 1: Configuration Details
- Appendix 2: DNS Records
- Appendix 3: Firewall and NAT Settings
- Appendix 4: Advanced Network Deployments
- Obtaining Documentation and Submitting a Service Request
- Cisco Legal Information
- Cisco Trademark
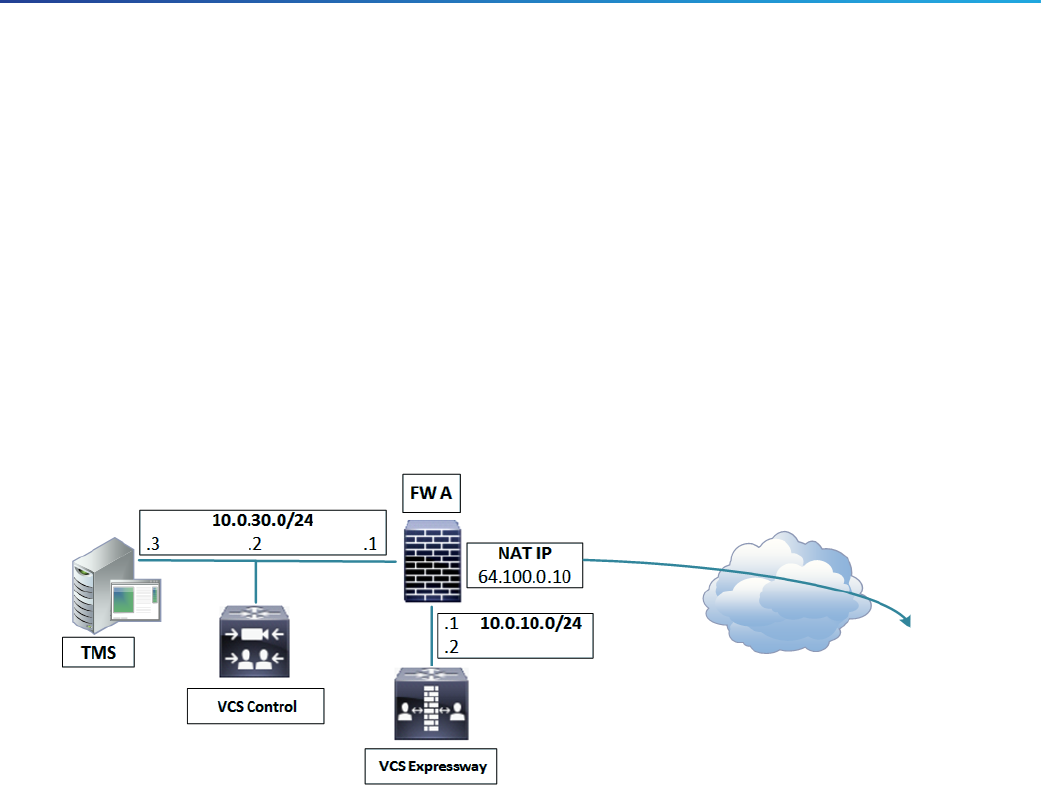
So, in this example, firewall A must allow NATreflection of traffic coming from the VCS Control that is destined for
the external address, that is 64.100.0.10, of the VCS Expressway. The traversal zone on the VCS Control must have
64.100.0.10 as the peer address.
The VCS Expressway should be configured with a default gateway of 10.0.10.1. Whether or not static routes are
needed in this scenario depends on the capabilities and settings of FW A and FW B. VCS Control to VCS Expressway
communications will be to the 64.100.0.10 address of the VCS Expressway. The return traffic from the VCS
Expressway to VCS Control might have to go through the default gateway. If a static route is added to the VCS
Expressway so that reply traffic goes from the VCS Expressway and directly through FW B to the 10.0.30.0/24
subnet, asymmetric routing occurs. Which may or may not work, depending on the firewall capabilities.
The VCS Expressway can be added to Cisco TMS using its internal IP address (10.0.10.3). This is because static NAT
mode settings on the VCS Expressway do not affect Cisco TMS management communications. You could add the
VCS Expressway's external interface to TMSinstead (64.100.0.10 in the diagram) if FW A allows it.
3-port Firewall DMZ Using Single VCS Expressway LAN Interface
In this deployment, a 3-port firewall is used to create the following:
■ DMZ subnet (10.0.10.0/24) with the following interfaces:
— DMZ interface of firewall A - 10.0.10.1
— LAN1 interface of VCS Expressway - 10.0.10.2
■ LAN subnet (10.0.30.0/24) with the following interfaces:
— LAN interface of firewall A - 10.0.30.1
— LAN1 interface of VCS Control – 10.0.30.2
— Network interface of Cisco TMS – 10.0.30.3
A static 1:1 NAT has been configured on firewall A, NATing the public address 64.100.0.10 to the LAN1 address of
the VCS Expressway. Static NAT mode is enabled for LAN1 on the VCS Expressway, with a static NAT address of
64.100.0.10.
The VCS Expressway should be configured with a default gateway of 10.0.10.1. Since this gateway must be used for
all traffic leaving the VCS Expressway, no static routes are needed in this type of deployment.
__________________________________________________________________
Note:The traversal client zone on the VCS Control needs to be configured with a peer address which matches the
static NAT address of the VCS Expressway, in this case 64.100.0.10, for the same reasons as described in Single
Subnet DMZ Using Single VCS Expressway LAN Interface and Static NAT, page 70.
This means that firewall A must allow traffic from the VCS Control with a destination address of 64.100.0.10. This
is also known as NAT reflection, and it should be noted that this is not supported by all types of firewalls.
__________________________________________________________________
71
Cisco VCS Expressway and VCS Control - Basic Configuration Deployment Guide
Appendix 4: Advanced Network Deployments