Manual
Table Of Contents
- Preface
- Introduction
- Process Summary
- Prerequisites
- Run the Service Setup Wizard
- VCS System Configuration
- Routing Configuration
- Pre-search Transforms
- Search Rules
- Task 8: Configuring Transforms
- Task 9: Configuring Local Zone Search Rules
- Task 10: Configuring the Traversal Zone
- Neighboring Between VCS Clusters
- Task 11: Configuring Traversal Zone Search Rules
- Task 12: Configuring the DNS Zone
- Task 13: Configuring DNS Zone Search Rules
- Task 14: Configuring External (Unknown) IP Address Routing
- Endpoint Registration
- System Checks
- Maintenance Routine
- Optional Configuration Tasks
- Appendix 1: Configuration Details
- Appendix 2: DNS Records
- Appendix 3: Firewall and NAT Settings
- Appendix 4: Advanced Network Deployments
- Obtaining Documentation and Submitting a Service Request
- Cisco Legal Information
- Cisco Trademark
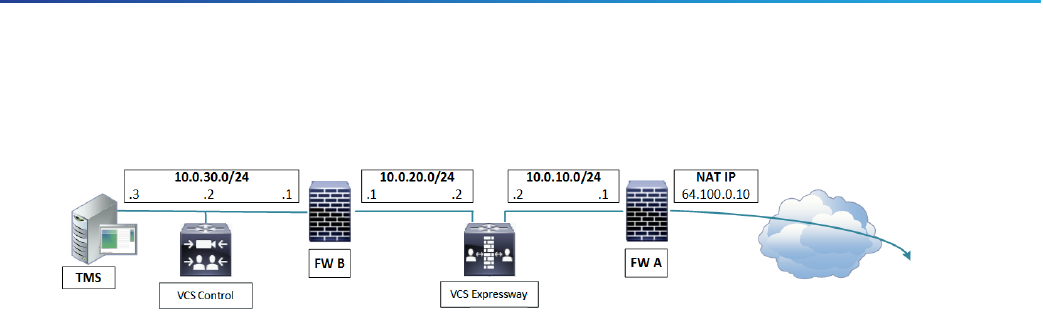
Figure 10 Dual Network Interfaces Deployment
This deployment consists of:
■ DMZ subnet 1 – 10.0.10.0/24, containing:
— the internal interface of Firewall A – 10.0.10.1
— the LAN2 interface of the VCS Expressway – 10.0.10.2
■ DMZ subnet 2 – 10.0.20.0/24, containing:
— the external interface of Firewall B – 10.0.20.1
— the LAN1 interface of the VCS Expressway – 10.0.20.2
■ LAN subnet – 10.0.30.0/24, containing:
— the internal interface of Firewall B – 10.0.30.1
— the LAN1 interface of the VCS Control – 10.0.30.2
— the network interface of the Cisco TMS server – 10.0.30.3
■ Firewall A is the outward-facing firewall; it is configured with a NAT IP (public IP) of 64.100.0.10 which is
statically NATed to 10.0.10.2 (the LAN2 interface address of the VCS Expressway)
■ Firewall B is the internally-facing firewall
■ VCS Expressway LAN1 has static NAT mode disabled
■ VCS Expressway LAN2 has static NAT mode enabled with Static NAT address 64.100.0.10
■ VCS Control has a traversal client zone pointing to 10.0.20.2 (LAN1 of the VCS Expressway)
■ Cisco TMS has VCS Expressway added with IP address 10.0.20.2
With the above deployment, there is no regular routing between the 10.0.20.0/24 and 10.0.10.0/24 subnets. The
VCS Expressway bridges these subnets and acts as a proxy for SIP/H.323 signaling and RTP/RTCP media.
Static Routes Towards the Internal Network
With a deployment like Figure 10 Dual Network Interfaces Deployment, page 64, you would typically configure the
private address of the external firewall (10.0.10.1 in the diagram) as the default gateway of the VCS Expressway.
Traffic that has no more specific route is sent out from either VCS Expressway interface to 10.0.10.1.
■ If the internal firewall (B) is doing NAT for traffic from the internal network (subnet 10.0.30.0 in diagram) to
LAN1 of the VCS Expressway (for example traversal client traffic from VCS Control), that traffic is recognized
as being from the same subnet (10.0.20.0 in diagram) as it reaches LAN1 of the VCS Expressway. The VCS
Expressway will therefore be able to reply to this traffic through its LAN1 interface.
■ If the internal firewall (B) is not doing NAT for traffic from the internal network (subnet 10.0.30.0 in diagram)
to LAN1 of the VCS Expressway (for example traversal client traffic from VCS Control), that traffic still has the
originating IPaddress (for example, 10.0.30.2 for traffic from VCS Control in the diagram). You must create a
static route towards that source from LAN1 on the VCS Expressway, or the return traffic will go to the default
gateway (10.0.10.1). You can do this on the web UI(System >Network interfaces >Static routes) or using
xCommand RouteAdd at the CLI.
If the VCS Expressway needs to communicate with other devices behind the internal firewall (eg. for reaching
network services such as NTP, DNS, LDAP/AD and syslog servers), you also need to add static routes from
VCS Expressway LAN1 to those devices/subnets.
64
Cisco VCS Expressway and VCS Control - Basic Configuration Deployment Guide
Appendix 4: Advanced Network Deployments










