Technical Manual
Verify
Identity Services Engine
The first connection triggers VA Scan. When the scan is finished, CoA Reauthentication is
triggered to apply new policy if it is matched.
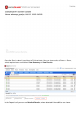
In order to verify which vulnerabilities were detected, navigate to Context Visibility > Endpoints.
Check per endpoints Vulnerabilities with the Scores given to it by Qualys.