User's Manual
Table Of Contents
- Table of Contents
- Chapter 1: Introduction
- Chapter 2: Connecting the Router
- Chapter 3: Configuring the PCs
- Chapter 4: Configuring the Router
- Chapter 5: Using the Router’s Web-Based Utility
- Appendix A: Troubleshooting
- Appendix B: How to Ping Your ISP’s E-mail and Web Addresses
- Appendix C: Configuring Wireless Security
- Appendix D: Finding the MAC Address and IP Address for Your Ethernet Adapter
- Appendix F: Glossary
- Appendix G: Specifications
- Appendix H: Warranty Information
- Appendix I: Contact Information
• Station MAC Filter. This option will allow you to prevent wireless users
on your network from accessing the Router’s functions.
Clicking the Active MAC Table button will display the MAC Addresses of
all users on your wireless network. Addresses in green show access to the
Router, while addresses in red do not have access.
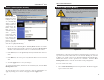
To filter users, click the Edit MAC Filter Setting button. The window
shown in Figure 5-24 will appear.
Click the Wireless MAC Entry drop-down menu to select a range of
entries for your network. From within this range, select the entry for which
you’d like to manage access. Verify that the appropriate MAC Address is
entered into the MAC Address field. Click the Filter checkbox beside that
MAC Address. Now, this user will be prevented from accessing the Router.
All other users will have access. To allow only that user and deny access to
all others, leave Filter unchecked.
Click the Apply button to set these changes or Undo if you do not wish
these changes to go into effect.
When finished with the Wireless Tab, click the Apply button to save the set-
tings. Otherwise, click the Cancel button to undo changes made on this screen.
Figure 5-24
Instant Wireless
®
Series
• Fragmentation Threshold. This value indicates how much of the Router’s
resources are devoted to recovering packet errors. The value should remain
at its default setting of 2,346. If you have decreased this value and experi-
ence high packet error rates, you can increase it again, but it will likely
decrease overall network performance. Only minor modifications of this
value are recommended.
• DTIM Interval. This value indicates the interval of the Delivery Traffic
Indication Message (DTIM). A DTIM field is a countdown field informing
clients of the next window for listening to broadcast and multicast mes-
sages. When the Router has buffered broadcast or multicast messages for
associated clients, it sends the next DTIM with a DTIM Interval value.
Clients for the Router hear the beacons and awaken to receive the broadcast
and multicast messages.
• Basic Rates. The basic transfer rates should be set depending on the speed
of your wireless network. You must select 1-2 (Mbps) if you have older
802.11 compliant equipment on your network, such as wireless adapters
that support only 1 or 2 Mbps. Selecting 1-2 (Mbps), however, does not
limit the basic transfer rates of faster adapters.
• TX Rates. Select all the supported rates at which the Router will commu-
nicate with your wireless network.
• Preamble Type. The preamble defines the length of the CRC block for
communication between the Router and the roaming Network Card. (High
network traffic areas should use the shorter preamble type.) Select the
appropriate preamble type and click the Apply button to set it.
• Authentication Type. You may choose between Open System, Shared
Key, and Both. The Authentication Type default is set to Open System, in
which the sender and the recipient do NOT share a secret key. Each party
generates its own key-pair and asks the receiver to accept the randomly-
generated key. Once accepted, this key is used for a short time only. Then
a new key is generated and agreed upon. Shared Key is when both the
sender and the recipient share a secret key.
• Antenna Selection. This selection is for choosing which antenna transmits
data. By default, the Diversity Antenna selection, used to increase recep-
tion, is chosen.
50
Wireless-B Broadband Router
49